このページには自動翻訳されたコンテンツが含まれています。 誤りを見つけた場合は、その箇所を選択して Ctrl+Enter を押し、編集者に報告してください。
10 Zabbixでネットワークスイッチやルーターを監視する
はじめに
このガイドでは、Zabbix を使用してネットワークスイッチやルーターの基本的な監視を開始するために必要な手順を説明します。 ここでは Cisco ルーターを例にしていますが、この手順は SNMP 対応のネットワーク機器すべてに適用できます。
このガイドの対象者
このガイドは、ネットワーク機器の基本的な監視を迅速に有効化したい新しい Zabbix ユーザーやネットワーク管理者向けに作成されています。 高度なカスタマイズや詳細な設定オプションが必要な場合は、SNMP エージェントページや Zabbix マニュアルの設定セクションを参照してください。
前提条件
このガイドを進める前に、以下を確認してください。
- Zabbix サーバーおよび Zabbix フロントエンドがインストールされていること:お使いの OS の手順に従ってインストールしてください(パッケージからのインストールおよびWeb インターフェースのインストールを参照)。
- SNMP 対応機器:SNMP が有効なネットワークスイッチまたはルーター(例:Cisco ルーター)。
- MIB ファイルがインストールされていること:MIB ファイルをインストールすると、Zabbix で数値 OID を人間が読める名前や説明に変換できるようになります。 適切な MIB サポートがない場合、数値のみが表示され、アイテムの設定やトラブルシューティングが困難になります。
Ubuntu で MIB ファイルをインストールするには:
1. MIB ダウンローダーパッケージをインストールします。
ベンダー固有の MIB(例:Cisco、Juniper)を追加する必要がある場合は、適切な MIB ディレクトリに配置してください。
- Linux ベースのシステムでは、一般的な場所は /usr/share/snmp/mibs/ または /usr/local/share/snmp/mibs/ です。
- Zabbix インストールの場合、MIB ファイルは /var/lib/zabbix/mibs/ に保存できます。
MIBDIRS 環境変数または snmp.conf ファイルに正しいパスが含まれていることを確認してください。
新しい MIB をシステムが認識しているか確認するには、以下を使用します。
詳細な手順については、お使いの SNMP ライブラリのドキュメントを参照してください。
2. /etc/snmp/snmp.conf を編集し、mibs : で始まる行をコメントアウトして、システムがすべての利用可能な MIB を読み込めるようにします。
3. snmpwalk(例:snmpwalk -v 2c -c <your_community_string> <device_IP>)を実行し、OID が説明的な名前で表示されることを確認します。
このガイドは、以下のセットアップに基づいています。
- Zabbix バージョン:7.2(パッケージからインストール)
- OS ディストリビューション:Ubuntu
- OS バージョン:24.04.2+
- Zabbix コンポーネント:サーバー、フロントエンド、および(ローカルネットワークメトリクスを監視する場合は)エージェント
- データベース:MySQL
- Web サーバー:Apache
- ネットワーク機器:Cisco Catalyst 3750V2-24FS
ネットワーク機器がすでに物理的に設置され、接続されていることを前提としています。
ネットワークデバイスの設定(Ciscoルーターの例)
SNMP経由で監視するには、ネットワークデバイスを設定してSNMPクエリを許可する必要があります。 以下の例はSNMPv2用であり、既存の設定は考慮されていません。 注意:これらのコマンドを適用すると、現在のSNMP設定が上書きされる場合があります。
Ciscoルーターの場合、設定は通常以下の手順で行います。
SNMPv2の例
1. SNMPを有効にし、コミュニティ文字列を設定します。
Ciscoルーターのコンソールにログインし、設定モードに入ります。
次に、読み取り専用のコミュニティ文字列を指定してSNMPを有効にします。 例:
<your_community_string> を安全なコミュニティ文字列に置き換えてください。 注:RO(読み取り専用)オプションは、SNMPがデバイスからデータを取得できるようにしますが、設定の変更はできません。
セキュリティ上の理由から、必要なデバイスのみにSNMPアクセスを制限することを推奨します。 アクセスコントロールリスト(ACL)の設定に関する詳細は、Ciscoの公式ドキュメントを参照してください。
2. 設定を保存します。
SNMP設定が再起動後も保持されるように、変更を保存します。
SNMPv3の例
SNMPv3は認証と暗号化による強化されたセキュリティを提供します。 その設定はSNMPv2よりも安全であり、デバイス固有のドキュメントで確認する必要があります。
1. SNMPグループの作成
プライバシー(暗号化)を有効にしたSNMPv3グループを設定します。
2. SNMPユーザーの作成
認証とプライバシーを持つSNMPv3ユーザーを追加します。 プレースホルダーを希望の値に置き換えてください。
3. 設定の保存
詳細やモデル固有の手順については、外部のCisco SNMP設定チュートリアルを参照してください。 このガイドでは、SNMP監視を有効にするための基本的な手順を提供しています。
Zabbixフロントエンドの設定
Zabbixフロントエンドでホストを作成する
1. Zabbixフロントエンドにログインします。
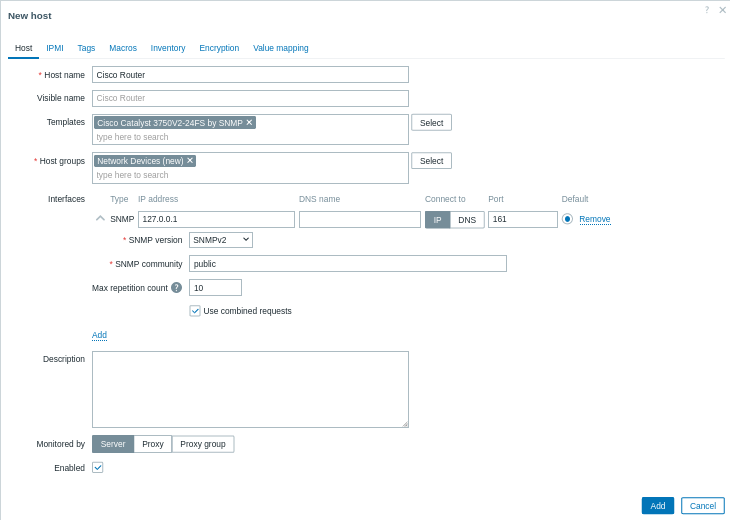
2. 新しいホストを追加します。
データ収集 > ホストに移動し、ホストの作成をクリックします。
- ホスト名: デバイスの名前を入力します(例: "Cisco Router")。
- ホストグループ: 既存のグループを選択するか、「ネットワークデバイス」などの新しいグループを作成します。
- インターフェース:
- インターフェースの下の追加をクリックします。
- インターフェースタイプとしてSNMPを選択します。
- CiscoルーターのIPアドレスまたはDNS名を入力します。
- デフォルトのSNMPポート(通常は161)を設定します。
- ドロップダウンメニューから適切なSNMPバージョン(例: SNMPv2)を選択します。
- SNMPv1/v2の場合は、SNMPコミュニティフィールドにコミュニティ文字列を入力します。 SNMPv3の場合は、追加の認証情報(コンテキスト名、セキュリティ名、セキュリティレベルなど)が求められます。
3. テンプレートのリンク
テンプレートフィールドで、デバイスに最も適したSNMPテンプレートを選択します。 Zabbixには、多くのデバイスファミリー向けに事前構築されたSNMPテンプレートが用意されています。 たとえば、Ciscoデバイスを監視する場合は、デバイスのOSやモデルに対応するテンプレート(Cisco IOS SNMPやCisco Catalyst 3750<device model> SNMPなど)を選択します。
4. 追加をクリックしてホストを保存します。

収集したメトリクスの表示
おめでとうございます!Zabbixはネットワークデバイスの監視を行うように設定されました。
最新データ:
- Zabbixフロントエンドで[監視] > [最新データ]に移動します。
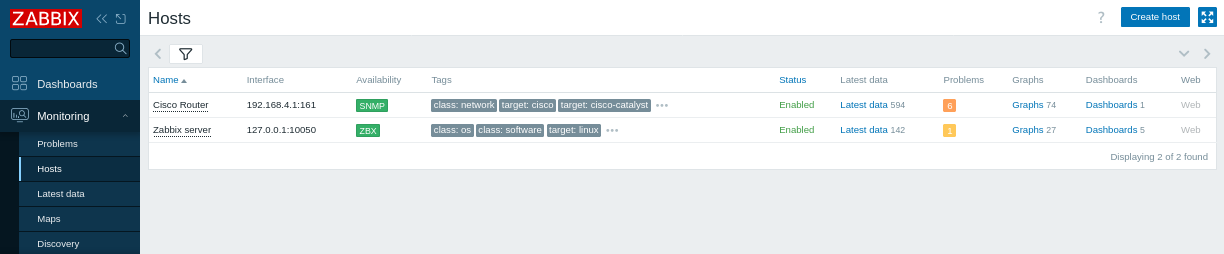
- “Cisco Router”ホスト(または検出されたホスト)を選択し、ハードウェアやネットワークの稼働時間、ICMP損失、ping、応答時間などのメトリクスを表示します。
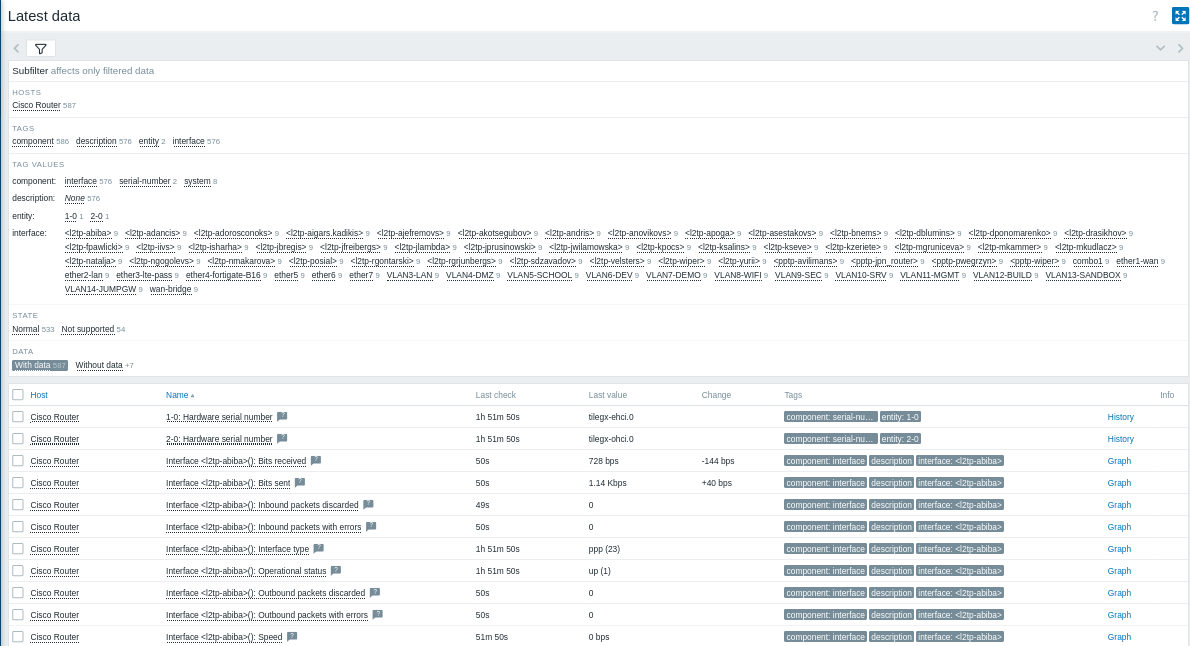
- グラフとスクリーン:
パフォーマンスデータを可視化するには、SNMPアイテムの横にあるグラフをクリックして詳細なメトリクスを確認します。
次のステップとして、以下を行うことができます:
- 追加のメトリクスを監視するためにカスタムSNMPアイテムを追加します。
- 潜在的な問題について通知を受け取るために問題アラートを設定します。
SNMPアイテムの作成
ホストのセットアップが完了したら、特定のメトリックを監視するためのアイテムを作成できます。 注意: テンプレートを使用している場合、このステップは省略可能です。テンプレートにはすでにデフォルトのアイテムセットが含まれています。
1. SNMP OIDの特定:
snmpwalkコマンドを使用して、デバイス上で利用可能なOIDを一覧表示します。 例:
監視したいメトリックのOIDを探します(例: ポート3の受信トラフィックの場合はIF-MIB::ifHCInOctets.3)。 数値OIDを取得するには、次のコマンドを使用できます:
2. SNMPアイテムの作成:
- データ収集 > ホストに移動し、SNMPホストのアイテムタブをクリックしてアイテムの作成をクリックします。
- 名前: わかりやすい名前を入力します(例:「ポート3受信トラフィック」)。
- タイプ: SNMPエージェントを選択します。
- キー: 意味のあるキーを指定します(例:
cisco.ifHCInOctets.3)。 - ホストインターフェース: SNMPインターフェースが選択されていることを確認します。
- SNMP OID: サポートされている形式のいずれかでOIDを入力します。例:
- 単一値の場合は
get[1.3.6.1.2.1.31.1.1.1.6.3]; - 非同期で値のサブツリーを取得する場合は
walk[1.3.6.1.2.1.31.1.1.1.6.3]。
- 単一値の場合は

- 前処理(必要に応じて): アイテムが累積カウンター(インターフェーストラフィックなど)を返す場合は、前処理タブに移動し、「1秒あたりの変化量」などの前処理ステップを追加してレートを計算します。

1回のSNMPトランザクションで複数の値を取得するには、walk[OID1,OID2,...]の構文で複数のOIDを指定できます。
数値OIDとMIB名の相互変換
SNMPを使用する際、数値OIDと対応するMIB名を相互に変換する必要がある場合があります。 この変換により、メトリクスの特定やトラブルシューティングが容易になります。
- MIB名を数値OIDに変換するには、
snmptranslateコマンドに-Onオプションを付けて使用します。 たとえば、MIB名IF-MIB::ifHCInOctets.3を数値OIDに変換するには、次のように実行します。
このコマンドの出力例:
- 数値OIDをMIB名に変換するには、
snmptranslateコマンドに-IR(または-m ALL)オプションを付けて逆変換します。 たとえば、数値OID.1.3.6.1.2.1.31.1.1.1.6.3をMIB名に変換するには、次のように実行します。
このコマンドの出力例:
障害アラートの設定
このガイドでは、メールアラートを送信するための基本的な設定手順を説明します。
1. ユーザー設定 > プロファイルに移動し、メディアタブに切り替えてメールアドレスを追加します。
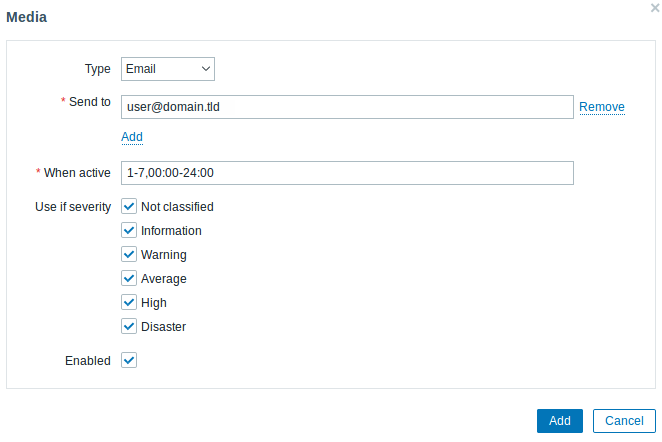
2. 障害通知の受信のガイドに従います。
次回、Zabbixが障害を検出したときに、メールでアラートを受信できるはずです。
設定をテストする
Zabbixがネットワークパフォーマンスの問題を正しく検出できることを確認するために、ICMP ping応答時間のしきい値を上げて実際の問題をシミュレートします。
1. Zabbixで「Cisco Router」ホストの設定を開きます。
2. マクロタブに移動し、継承されたホストマクロを選択します。
3. {$ICMP_RESPONSE_TIME_WARN}マクロ(または同様の応答時間しきい値マクロ)を探します。
4. 非常に低い値(例:0.001)を設定し、ping応答がこの値を超えた場合にアラートが発生するようにします。
5. 更新をクリックして変更を適用します。
6. Zabbixがシミュレートされた問題を検出するまでしばらく待ちます。
7. 監視 > 障害に移動し、アラートが表示されることを確認します(例:「ICMP ping応答時間が高い」)。
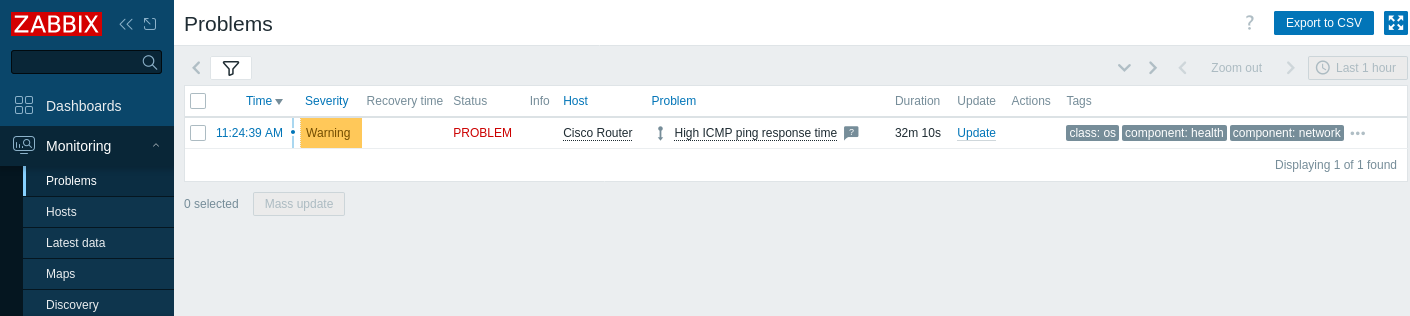
アラートが設定されている場合は、問題アラートも受信するはずです。
8. マクロ値を元の設定に戻し、更新をクリックして変更を保存します。
9. 問題が解決され、障害セクションから消えることを確認します。
SNMP監視のトラブルシューティング
ZabbixフロントエンドのSNMPアイコンが赤色で表示されたり、データが収集されない場合は、以下の手順をお試しください。
1. SNMPの接続性を確認します。
SNMPv2の場合、Zabbixサーバーから以下のコマンドを実行します。
このコマンドは、デバイスがSNMPクエリに応答するかどうかを確認します。
SNMPv3の場合は、適切なSNMPv3認証情報を含めてください。
snmpwalk -v3 -u <your_user> -l authPriv -a MD5 -A <auth_password> -x AES -X <priv_password> <device_IP> .これにより、SNMPv3の認証情報が正しいことと、デバイスが安全に応答していることを確認できます。
2. 前提条件で説明したように、MIBファイルがインストールされ有効になっていることを確認します。 ネットワークデバイスにクエリを実行した際、以下のコマンドでエラーが出ないことを確認してください。
これにより、エラーなくOIDが翻訳されて返されるはずです。
3. Zabbixで設定したSNMPバージョンと認証情報が、デバイス側の設定と一致していることを確認します。 たとえば、Zabbixのホスト設定でSNMPの設定を確認し、デバイスの設定と照合してください。 Ciscoデバイスの場合、以下のコマンドでSNMP設定を確認できます。
これにより、コミュニティ文字列(SNMPv2の場合)やSNMPv3ユーザー情報が正しいことを確認できます。
4. ネットワークデバイスでSNMPが正しく有効になっていることを確認します。 Ciscoルーターの場合、コンソールにログインして以下を実行します。
このコマンドは、アクティブなSNMP設定を表示し、SNMPが正しく設定されているかどうかを確認するのに役立ちます。
5. Zabbixサーバーとデバイス間で、ファイアウォールやネットワークの問題によりSNMPトラフィック(通常はポート161)がブロックされていないことを確認します。 接続性は以下でテストできます。
nc -zv <device_IP> 161
nc -zvは、デバイスのポート161が開いていてリッスンしているかどうかを確認します。
また、UbuntuでUFWを使用している場合は、ファイアウォールの状態を確認してください。
または、iptablesの場合は以下を実行します。
6. 問題の特定に役立つSNMP関連のエラーがないか、Zabbixサーバーのログファイルを確認します。
tail -fは、リアルタイムでログの更新を監視できます。
関連情報:
- アイテムの作成 - 追加のメトリクスを追加する方法について説明します。
- SNMPエージェント - ZabbixによるSNMP監視に関する追加情報。
- ネットワークデバイス用の標準化テンプレート - 利用可能なSNMPテンプレートに関する情報。
- SNMP OIDのディスカバリ - スイッチでのSNMPディスカバリに関する追加情報。
- ネットワークディスカバリルールの設定 - Zabbixがホストやサービスを検出するために使用するネットワークディスカバリルールの設定方法に関する追加情報。

