Join our translation project and help translate Zabbix documentation into your native language.
4 MFA
Overview
Multi-factor authentication (MFA) can be used to sign in to Zabbix, providing an additional layer of security beyond just a username and password.
With MFA, the user must exist in Zabbix, must provide Zabbix credentials when logging in, and must also prove their identity by other means, usually, a code generated by an authenticator app on the user's phone.
Multiple MFA methods are available, allowing users to choose the option that best fits their security requirements and preferences. These methods are Time-Based One-Time Password (TOTP) and Duo Universal Prompt.
Configuration
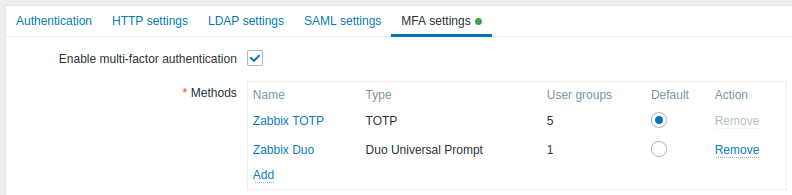
Configuration parameters:
| Parameter | Description |
|---|---|
| Enable multi-factor authentication | Mark the checkbox to enable multi-factor authentication. |
| Methods | Click Add to configure an MFA method (see method configuration below). |
Method configuration
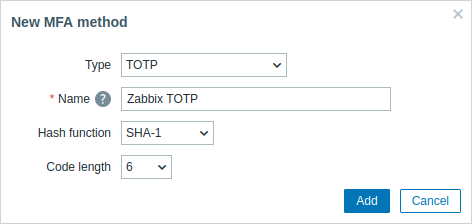
Method configuration parameters:
| Parameter | Description |
|---|---|
| Type | Select the type of MFA method: TOTP - use an authenticator app to generate time-based one-time passwords; Duo Universal Prompt - use the Duo authentication service to provide multi-factor authentication. |
| Name | Enter a name that is displayed as the account name to all MFA users in authenticator apps (for example, "Zabbix"). |
| Hash function | Select the hash function (SHA-1, SHA-256, or SHA-512) for generating TOTP codes. This parameter is available if the MFA method type is set to "TOTP". Note that choosing SHA-256 or SHA-512 may significantly limit compatibility, as many applications currently do not support these functions. |
| Code length | Select the verification code length (6 or 8). This parameter is available if MFA method type is set to "TOTP". |
| API hostname | Enter the API hostname provided by the Duo authentication service. This parameter is available if MFA method type is set to "Duo Universal Prompt". |
| Client ID | Enter the client ID provided by the Duo authentication service. This parameter is available if MFA method type is set to "Duo Universal Prompt". |
| Client secret | Enter the client secret provided by the Duo authentication service. This parameter is available if MFA method type is set to "Duo Universal Prompt". |
Configuration examples
This section provides examples of configuring MFA using Time-Based One-Time Password (TOTP) and Duo Universal Prompt.
TOTP
For TOTP, users must verify their identity using an authenticator app (for example, the Google Authenticator app).
1. Go to the MFA settings in Zabbix under Users → Authentication and enable multi-factor authentication.
2. Add a new MFA method with the following configuration:
- Type: TOTP
- Name: Zabbix TOTP
- Hash function: SHA-1
- Code length: 6
3. Go to Users → User groups and create a new user group with the following configuration:
- Group name: TOTP group
- Users: Admin
- Multi-factor authentication: Default (or "Zabbix TOTP" if it is not set as default)
4. Log out of Zabbix and log back in using your credentials. Upon successful login, you will be prompted to enroll in MFA, displaying a QR code and a secret key.
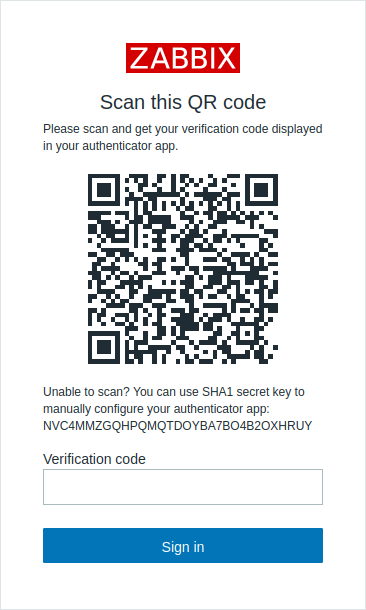
5. Scan the QR code or enter the secret key into the Google Authenticator app. The app will generate a verification code which you should enter to complete the login process.
6. For subsequent logins, retrieve the verification code from the Google Authenticator app and enter it during login.
Duo Universal Prompt
For Duo Universal Prompt, users must verify their identity using the Duo Mobile authenticator app.
The Duo Universal Prompt MFA method requires the installation of the php-curl extension, access to Zabbix over HTTPS, and permission for outbound connections to Duo servers. Moreover, if you have enabled Content Security Policy (CSP) on the web server, make sure to add "duo.com" to the CSP directive in your virtual host's configuration file.
1. Signup for a free Duo admin account at Duo Signup.
2. Open the Duo Admin Panel, go to Applications → Protect an Application, search for the Web SDK application, and click Protect.
3. Note the credentials (Client ID, Client secret, API hostname) required for configuring the MFA method in Zabbix.
4. Go to MFA settings in Zabbix under Users → Authentication and enable multi-factor authentication.
5. Add a new MFA method with the following configuration:
- Type: Duo Universal Prompt
- Name: Zabbix Duo
- API hostname: (use API hostname from Duo)
- Client ID: (use Client ID from Duo)
- Client secret: (use Client secret from Duo)
6. Go to Users → User groups and create a new user group with the following configuration:
- Group name: Duo group
- Users: Admin
- Multi-factor authentication: Default (or "Zabbix Duo" if it is not set as default)
7. Log out of Zabbix and log back in using your credentials. Upon successful login, you will be prompted to enroll in MFA and redirected to Duo. Complete the Duo setup and verify your user with your phone's Duo app to log in.
8. For subsequent logins, use the appropriate MFA method provided by the Duo app (such as retrieving a verification code, responding to push notifications, or using hard keys), and enter the required information during login.
