Is this not what you were looking for? Switch to the current version or choose one from the drop-down menu.
3 Authentication
Overview
The Administration → Authentication section allows to specify the global user authentication method to Zabbix and internal password requirements. The available methods are internal, HTTP, LDAP, and SAML authentication.
Default authentication
By default, Zabbix uses internal Zabbix authentication for all users. It is possible to change the default method to LDAP system-wide or enable LDAP authentication only for specific user groups.
To set LDAP as default authentication method for all users, navigate to the LDAP tab and configure authentication parameters, then return to the Authentication tab and switch Default authentication selector to LDAP.
Note that the authentication method can be fine-tuned on the user group level. Even if LDAP authentication is set globally, some user groups can still be authenticated by Zabbix. These groups must have frontend access set to Internal. Vice versa, if internal authentication is used globally, LDAP authentication details can be specified and used for specific user groups whose frontend access is set to LDAP. If a user is included into at least one user group with LDAP authentication, this user will not be able to use internal authentication method.
HTTP and SAML 2.0 authentication methods can be used in addition to the default authentication method.
Internal authentication
The Authentication tab allows defining custom password complexity requirements for internal Zabbix users.
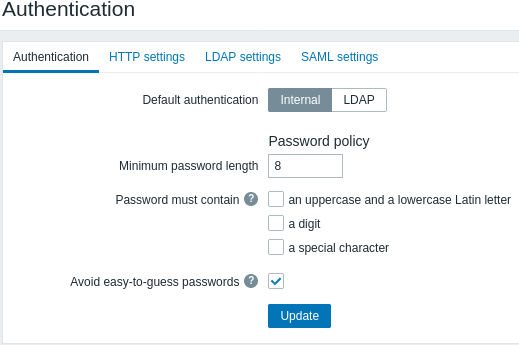
The following password policy options can be configured:
| Parameter | Description |
|---|---|
| Minimum password length | By default, the minimum password length is set to 8. Supported range: 1-70. Note that passwords longer than 72 characters will be truncated. |
| Password must contain | Mark one or several checkboxes to require usage of specified characters in a password: -an uppercase and a lowercase Latin letter -a digit -a special character Hover over the question mark to see a hint with the list of characters for each option. |
| Avoid easy-to-guess passwords | If marked, a password will be checked against the following requirements: - must not contain user's name, surname, or username - must not be one of the common or context-specific passwords. The list of common and context-specific passwords is generated automatically from the list of NCSC "Top 100k passwords", the list of SecLists "Top 1M passwords" and the list of Zabbix context-specific passwords. Internal users will not be allowed to set passwords included in this list as such passwords are considered weak due to their common use. |
Changes in password complexity requirements will not affect existing user passwords, but if an existing user chooses to change a password, the new password will have to meet current requirements. A hint with the list of requirements will be displayed next to the Password field in the user profile and in the user configuration form accessible from the Administration→Users menu.
HTTP authentication
HTTP or web server-based authentication (for example: Basic Authentication, NTLM/Kerberos) can be used to check user names and passwords. Note that a user must exist in Zabbix as well, however its Zabbix password will not be used.
Be careful! Make sure that web server authentication is configured and works properly before switching it on.
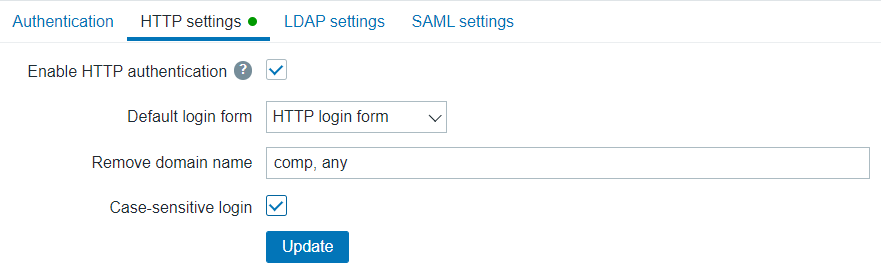
Configuration parameters:
| Parameter | Description |
|---|---|
| Enable HTTP authentication | Mark the checkbox to enable HTTP authentication. Hovering the mouse over  will bring up a hint box warning that in the case of web server authentication, all users (even with frontend access set to LDAP/Internal) will be authenticated by the web server, not by Zabbix. will bring up a hint box warning that in the case of web server authentication, all users (even with frontend access set to LDAP/Internal) will be authenticated by the web server, not by Zabbix. |
| Default login form | Specify whether to direct non-authenticated users to: Zabbix login form - standard Zabbix login page. HTTP login form - HTTP login page. It is recommended to enable web-server based authentication for the index_http.php page only. If Default login form is set to 'HTTP login page' the user will be logged in automatically if web server authentication module will set valid user login in the $_SERVER variable.Supported $_SERVER keys are PHP_AUTH_USER, REMOTE_USER, AUTH_USER. |
| Remove domain name | A comma-delimited list of domain names that should be removed from the username. E.g. comp,any - if username is 'Admin@any', 'comp\Admin', user will be logged in as 'Admin'; if username is 'notacompany\Admin', login will be denied. |
| Case sensitive login | Unmark the checkbox to disable case-sensitive login (enabled by default) for usernames. E.g. disable case-sensitive login and log in with, for example, 'ADMIN' user even if the Zabbix user is 'Admin'. Note that with case-sensitive login disabled the login will be denied if multiple users exist in Zabbix database with similar usernames (e.g. Admin, admin). |
For internal users who are unable to log in using HTTP credentials (with HTTP login form set as default) leading to the 401 error, you may want to add a ErrorDocument 401 /index.php?form=default line to basic authentication directives, which will redirect to the regular Zabbix login form.
LDAP authentication
External LDAP authentication can be used to check user names and passwords. Note that a user must exist in Zabbix as well, however its Zabbix password will not be used.
Several LDAP servers can be defined, if necessary. For example, a different server can be used to authenticate a different user group. Once LDAP servers are configured, in user group configuration it becomes possible to select the required LDAP server for the respective user group.
If a user is in multiple user groups and multiple LDAP servers, the first server in the list of LDAP servers sorted by name in ascending order will be used for authentication.
Zabbix LDAP authentication works at least with Microsoft Active Directory and OpenLDAP.
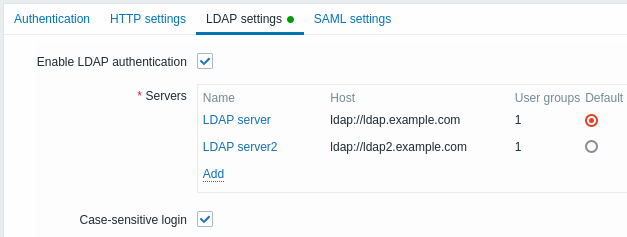
Configuration parameters:
| Parameter | Description |
|---|---|
| Enable LDAP authentication | Mark the checkbox to enable LDAP authentication. |
| Servers | Click on Add to configure an LDAP server (see LDAP server configuration parameters below). |
| Case-sensitive login | Unmark the checkbox to disable case-sensitive login (enabled by default) for usernames. E.g. disable case-sensitive login and log in with, for example, 'ADMIN' user even if the Zabbix user is 'Admin'. Note that with case-sensitive login disabled the login will be denied if multiple users exist in Zabbix database with similar usernames (e.g. Admin, admin). |
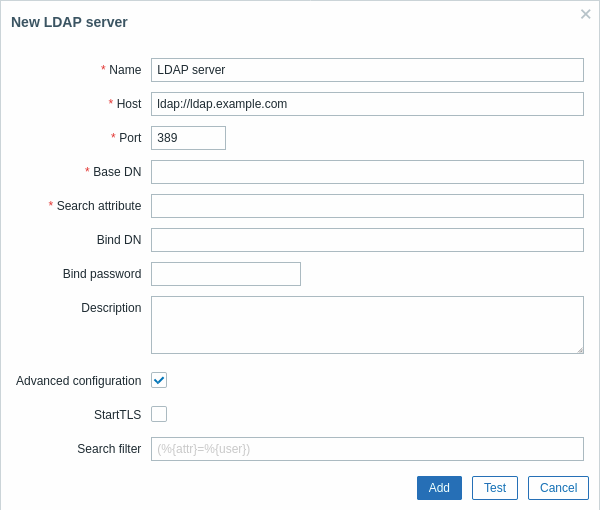
LDAP server configuration parameters:
| Parameter | Description |
|---|---|
| Name | Name of the LDAP server in Zabbix configuration. |
| Host | Host of the LDAP server. For example: ldap://ldap.example.com For secure LDAP server use ldaps protocol. ldaps://ldap.example.com With OpenLDAP 2.x.x and later, a full LDAP URI of the form ldap://hostname:port or ldaps://hostname:port may be used. |
| Port | Port of the LDAP server. Default is 389. For secure LDAP connection port number is normally 636. Not used when using full LDAP URIs. |
| Base DN | Base path to search accounts: ou=Users,ou=system (for OpenLDAP), DC=company,DC=com (for Microsoft Active Directory) |
| Search attribute | LDAP account attribute used for search: uid (for OpenLDAP), sAMAccountName (for Microsoft Active Directory) |
| Bind DN | LDAP account for binding and searching over the LDAP server, examples: uid=ldap_search,ou=system (for OpenLDAP), CN=ldap_search,OU=user_group,DC=company,DC=com (for Microsoft Active Directory) Anonymous binding is also supported. Note that anonymous binding potentially opens up domain configuration to unauthorized users (information about users, computers, servers, groups, services, etc.). For security reasons, disable anonymous binds on LDAP hosts and use authenticated access instead. |
| Bind password | LDAP password of the account for binding and searching over the LDAP server. |
| Description | Description of the LDAP server. |
| StartTLS | Mark the checkbox to use the StartTLS operation when connecting to LDAP server. The connection will fall if the server doesn't support StartTLS. StartTLS cannot be used with servers that use the ldaps protocol To access this option, mark the Advanced configuration checkbox first. |
| Search filter | Define a custom string when authenticating user in LDAP. The following placeholders are supported:%{attr} - search attribute name (uid, sAMAccountName)%{user} - user username value to authenticate.If omitted then LDAP will use the default filter: (%{attr}=%{user})To access this option, mark the Advanced configuration checkbox first. |
The Test button allows to test user access:
| Parameter | Description |
|---|---|
| Login | LDAP user name to test (prefilled with the current user name from Zabbix frontend). This user name must exist in the LDAP server. Zabbix will not activate LDAP authentication if it is unable to authenticate the test user. |
| User password | LDAP user password to test. |
In case of trouble with certificates, to make a secure LDAP connection (ldaps) work you may need to add a TLS_REQCERT allow line to the /etc/openldap/ldap.conf configuration file. It may decrease the security of connection to the LDAP catalog.
It is recommended to create a separate LDAP account (Bind DN) to perform binding and searching over the LDAP server with minimal privileges in the LDAP instead of using real user accounts (used for logging in the Zabbix frontend).
Such an approach provides more security and does not require changing the Bind password when the user changes his own password in the LDAP server.
In the table above it's ldap_search account name.
SAML authentication
SAML 2.0 authentication can be used to sign in to Zabbix. Note that a user must exist in Zabbix, however, its Zabbix password will not be used. If authentication is successful, then Zabbix will match a local username with the username attribute returned by SAML.
If SAML authentication is enabled, users will be able to choose between logging in locally or via SAML Single Sign-On.
Setting up the identity provider
In order to work with Zabbix, a SAML identity provider (onelogin.com, auth0.com, okta.com, etc.) needs to be configured in the following way:
- Assertion Consumer URL should be set to
<path_to_zabbix_ui>/index_sso.php?acs - Single Logout URL should be set to
<path_to_zabbix_ui>/index_sso.php?sls
<path_to_zabbix_ui> examples: https://example.com/zabbix/ui, http://another.example.com/zabbix, http://<any\_public\_ip\_address>/zabbix
Setting up Zabbix
It is required to install php-openssl if you want to use SAML authentication in the frontend.
To use SAML authentication Zabbix should be configured in the following way:
1. Private key and certificate should be stored in the ui/conf/certs/, unless custom paths are provided in zabbix.conf.php.
By default, Zabbix will look in the following locations:
- ui/conf/certs/sp.key - SP private key file
- ui/conf/certs/sp.crt - SP cert file
- ui/conf/certs/idp.crt - IDP cert file
2. All of the most important settings can be configured in the Zabbix frontend. However, it is possible to specify additional settings in the configuration file.
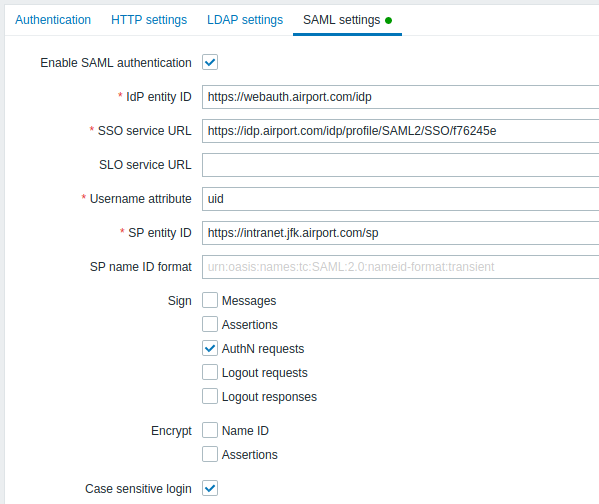
Configuration parameters, available in the Zabbix frontend:
| Parameter | Description |
|---|---|
| Enable SAML authentication | Mark the checkbox to enable SAML authentication. |
| IDP entity ID | The unique identifier of SAML identity provider. |
| SSO service URL | The URL users will be redirected to when logging in. |
| SLO Service URL | The URL users will be redirected to when logging out. If left empty, the SLO service will not be used. |
| // Username attribute// | SAML attribute to be used as a username when logging into Zabbix. List of supported values is determined by the identity provider. Examples: uid userprincipalname samaccountname username userusername urn:oid:0.9.2342.19200300.100.1.1 urn:oid:1.3.6.1.4.1.5923.1.1.1.13 urn:oid:0.9.2342.19200300.100.1.44 |
| SP entity ID | The unique identifier of SAML service provider. |
| SP name ID format | Defines which name identifier format should be used. Examples: urn:oasis:names:tc:SAML:2.0:nameid-format:persistent urn:oasis:names:tc:SAML:2.0:nameid-format:transient urn:oasis:names:tc:SAML:2.0:nameid-format:kerberos urn:oasis:names:tc:SAML:2.0:nameid-format:entity |
| Sign | Mark the checkboxes to select entities for which SAML signature should be enabled: Messages Assertions AuthN requests Logout requests Logout responses |
| Encrypt | Mark the checkboxes to select entities for which SAML encryption should be enabled: Assertions Name ID |
| Case-sensitive login | Mark the checkbox to enable case-sensitive login (disabled by default) for usernames. E.g. disable case-sensitive login and log in with, for example, 'ADMIN' user even if the Zabbix user is 'Admin'. Note that with case-sensitive login disabled the login will be denied if multiple users exist in Zabbix database with similar usernames (e.g. Admin, admin). |
Advanced settings
Additional SAML parameters can be configured in the Zabbix frontend configuration file (zabbix.conf.php):
- $SSO['SP_KEY'] = '<path to the SP private key file>';
- $SSO['SP_CERT'] = '<path to the SP cert file>';
- $SSO['IDP_CERT'] = '<path to the IDP cert file>';
- $SSO['SETTINGS']
Zabbix uses OneLogin's SAML PHP Toolkit library (version 3.4.1). The structure of $SSO['SETTINGS'] section should be similar to the structure used by the library. For the description of configuration options, see official library documentation.
Only the following options can be set as part of $SSO['SETTINGS']:
- strict
- baseurl
- compress
- contactPerson
- organization
- sp (only options specified in this list)
- attributeConsumingService
- x509certNew
- idp (only options specified in this list)
- singleLogoutService (only one option)
- responseUrl
- certFingerprint
- certFingerprintAlgorithm
- x509certMulti
- singleLogoutService (only one option)
- security (only options specified in this list)
- signMetadata
- wantNameId
- requestedAuthnContext
- requestedAuthnContextComparison
- wantXMLValidation
- relaxDestinationValidation
- destinationStrictlyMatches
- rejectUnsolicitedResponsesWithInResponseTo
- signatureAlgorithm
- digestAlgorithm
- lowercaseUrlencoding
All other options will be taken from the database and cannot be overridden. The debug option will be ignored.
In addition, if Zabbix UI is behind a proxy or a load balancer, the custom use_proxy_headers option can be used:
- false (default) - ignore the option;
- true - use X-Forwarded-* HTTP headers for building the base URL.
If using a load balancer to connect to Zabbix instance, where the load balancer uses TLS/SSL and Zabbix does not, you must indicate 'baseurl', 'strict' and 'use_proxy_headers' parameters as follows:
$SSO['SETTINGS']=['strict' => false, 'baseurl' => "https://zabbix.example.com/zabbix/", 'use_proxy_headers' => true]Configuration example:
