Installation with OpenShift
Overview
Zabbix helps you to do a real-time monitoring of millions of metrics collected from tens of thousands of servers, virtual machines and network devices. The Zabbix Operator allows users to easily deploy, manage, and maintain Zabbix deployments on OpenShift. By installing this integration you will be able to deploy Zabbix server/proxies and other components with a single command.
Supported features
Zabbix Operator comes with a few possible installation options:
- Zabbix server - a simple Zabbix installation with included Zabbix server, Zabbix web interface and Zabbix Java gateway with MySQL database support. The feature does not provide MySQL service and requires an external MySQL database.
- Zabbix server (full) - a Zabbix installation with included Zabbix server, Zabbix web interface, Zabbix Java gateway and MySQL server instance.
- Zabbix proxy (SQLite3) - a very simple way to gain power of Zabbix proxy. The feature has SQLite3 support for Zabbix proxies and allows to specify the amount of proxies.
- Zabbix proxy (MySQL) - another option of Zabbix proxy. This option supports and delivers a MySQL database. It is possible to use a built-in MySQL database instance or an external one.
- Zabbix agent - a Zabbix agent can be deployed on each available node for stability and performance monitoring on remote nodes. It allows to gather metrics with full automation!
- Zabbix appliance - a Zabbix appliance is a very simple way to test and check Zabbix features. This option provides all the core components in one solution. It includes Zabbix server, Zabbix Java gateway, Zabbix web interface and MySQL server in deployment. It is very useful for testing Zabbix features!
Currently Zabbix Operator is based on the Zabbix 5.0 LTS version and supports OpenShift 4.0, 4.1, 4.2, 4.3, 4.4 and 4.5.
Installing Zabbix Operator
Using RedHat Marketplace
The installation of Zabbix Operator using Red Hat Marketplace requires the OpenShift cluster to be registered in the Marketplace Portal, including the roll out of the PullSecret in your cluster. Failure to do so will result in an image pull authentication failure with the Red Hat registry.
1. Select the OperatorHub from the Operators submenu and search for Zabbix.
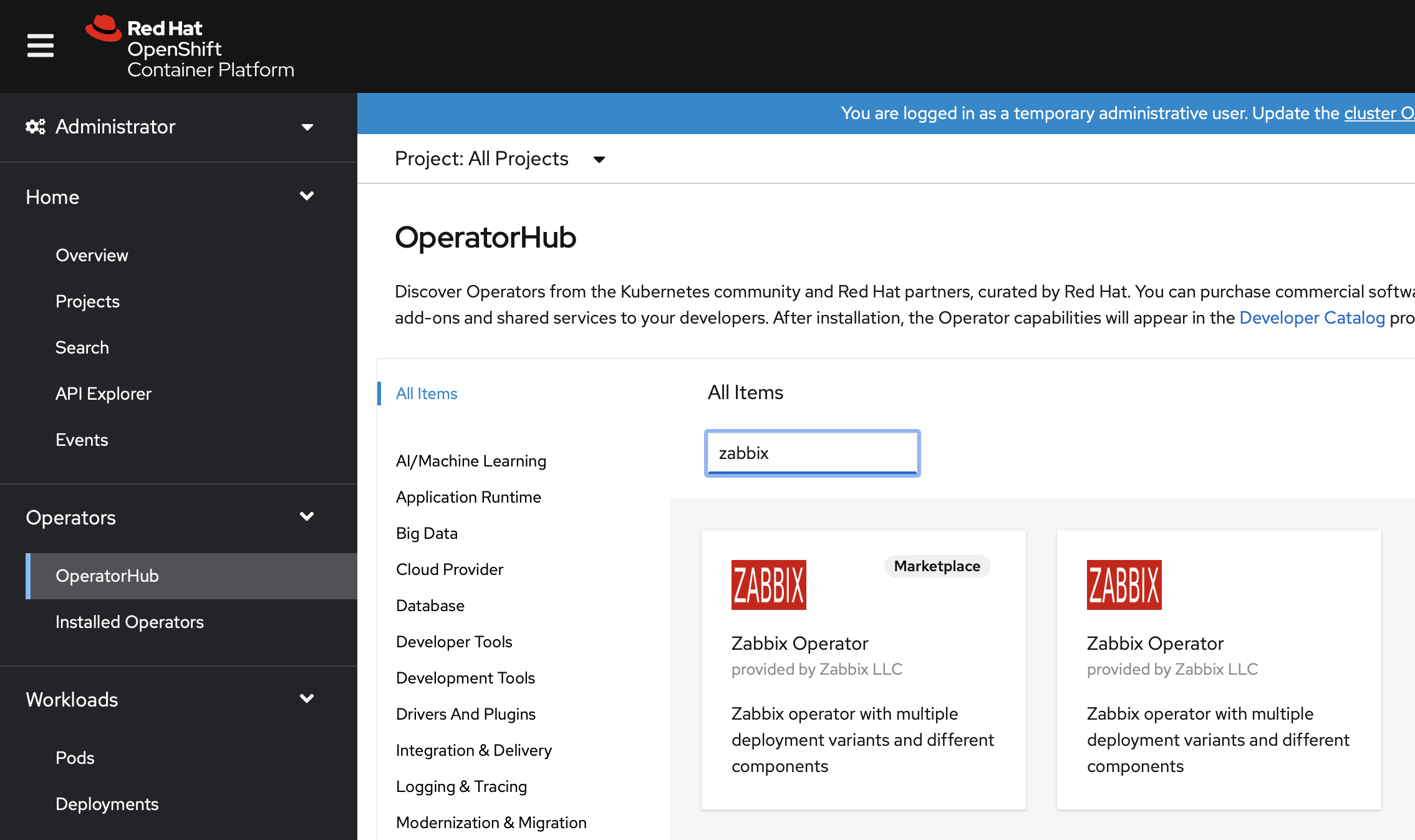
Choose the RedHat Marketplace option.
2. Select "Zabbix Operator" and click on Purchase.
Openshift needs to be registered with the Red Hat Marketplace portal.
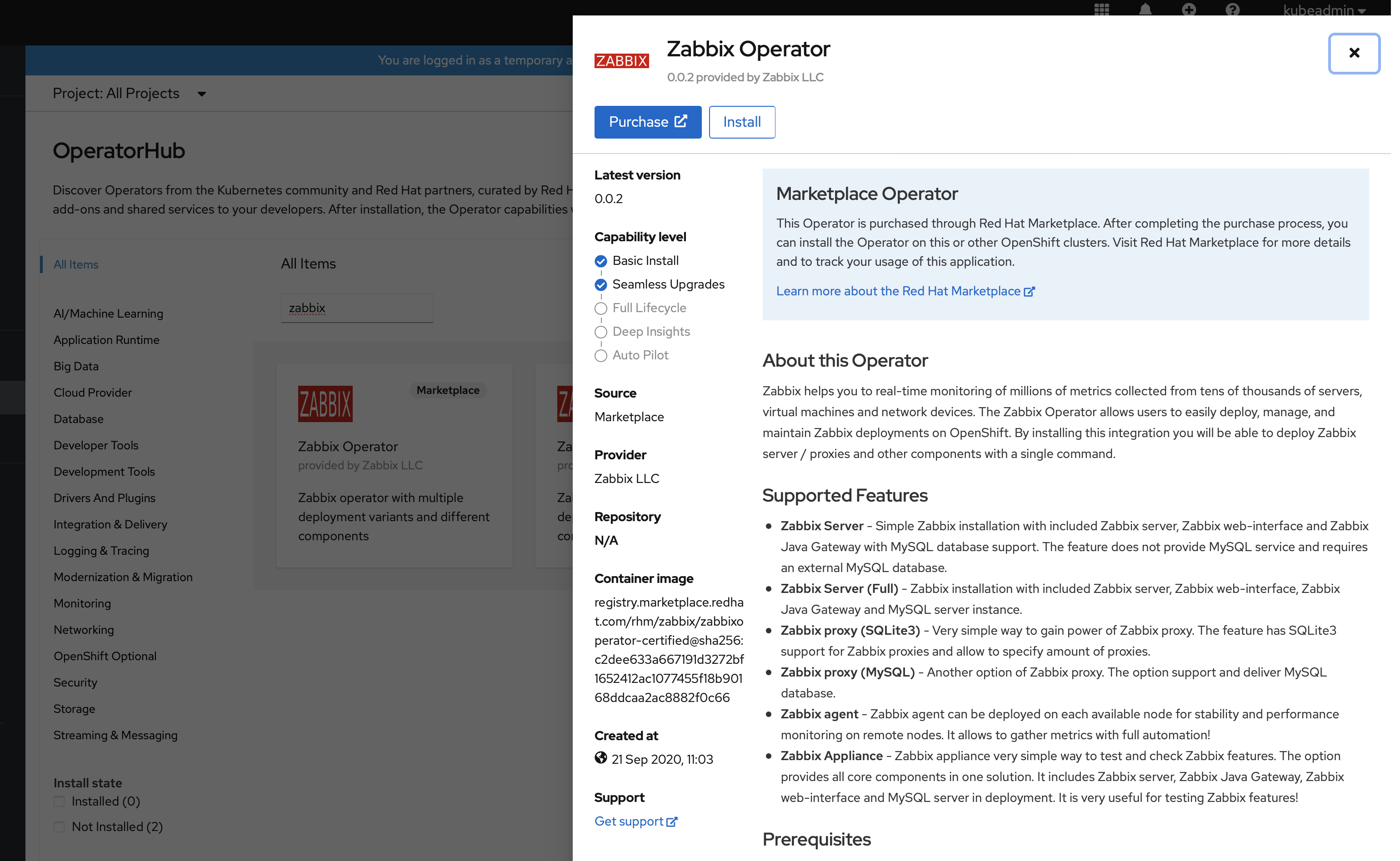
3. Select the most suitable install option.
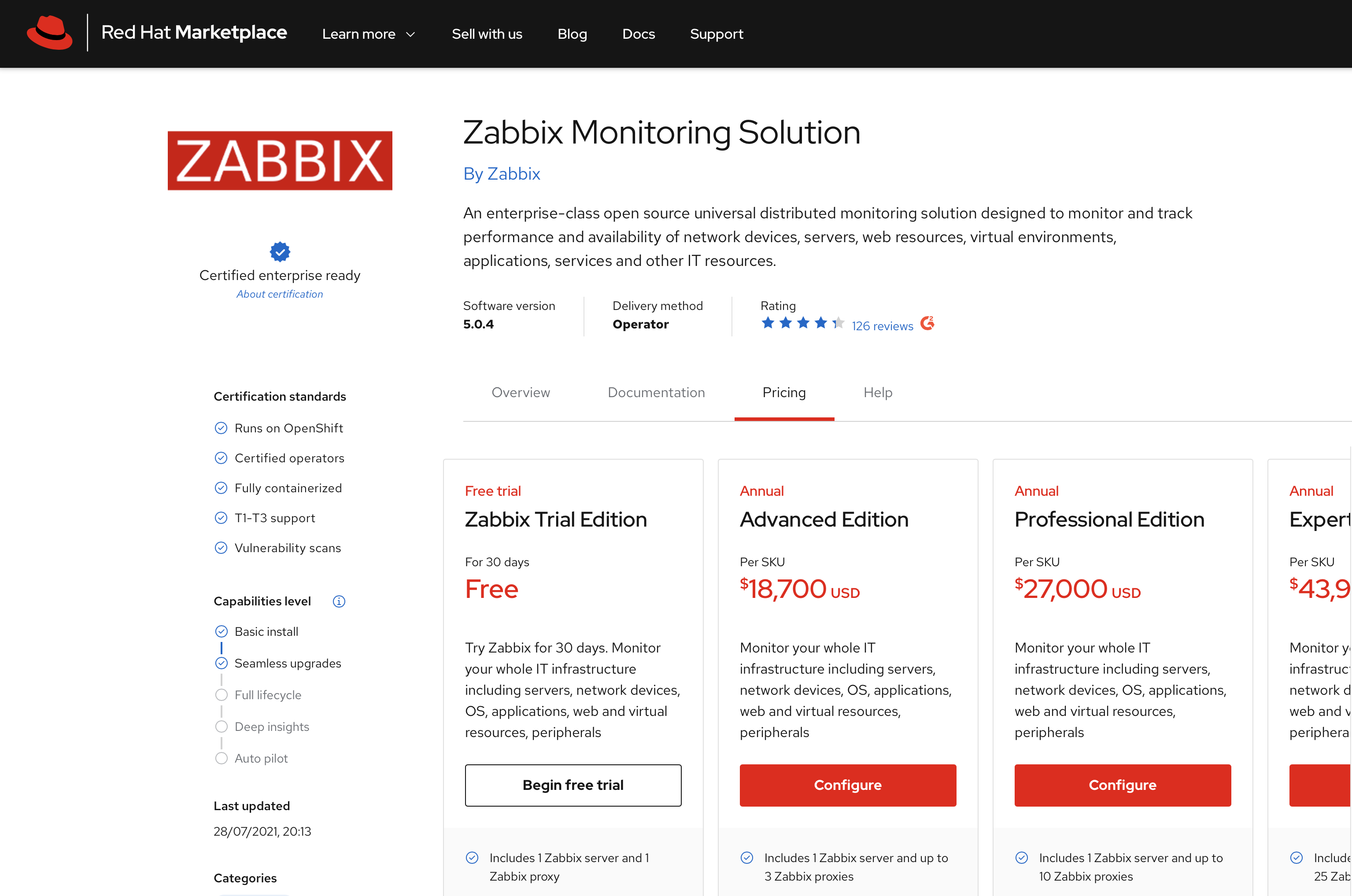
4. Specify the product configuration to fit your needs.
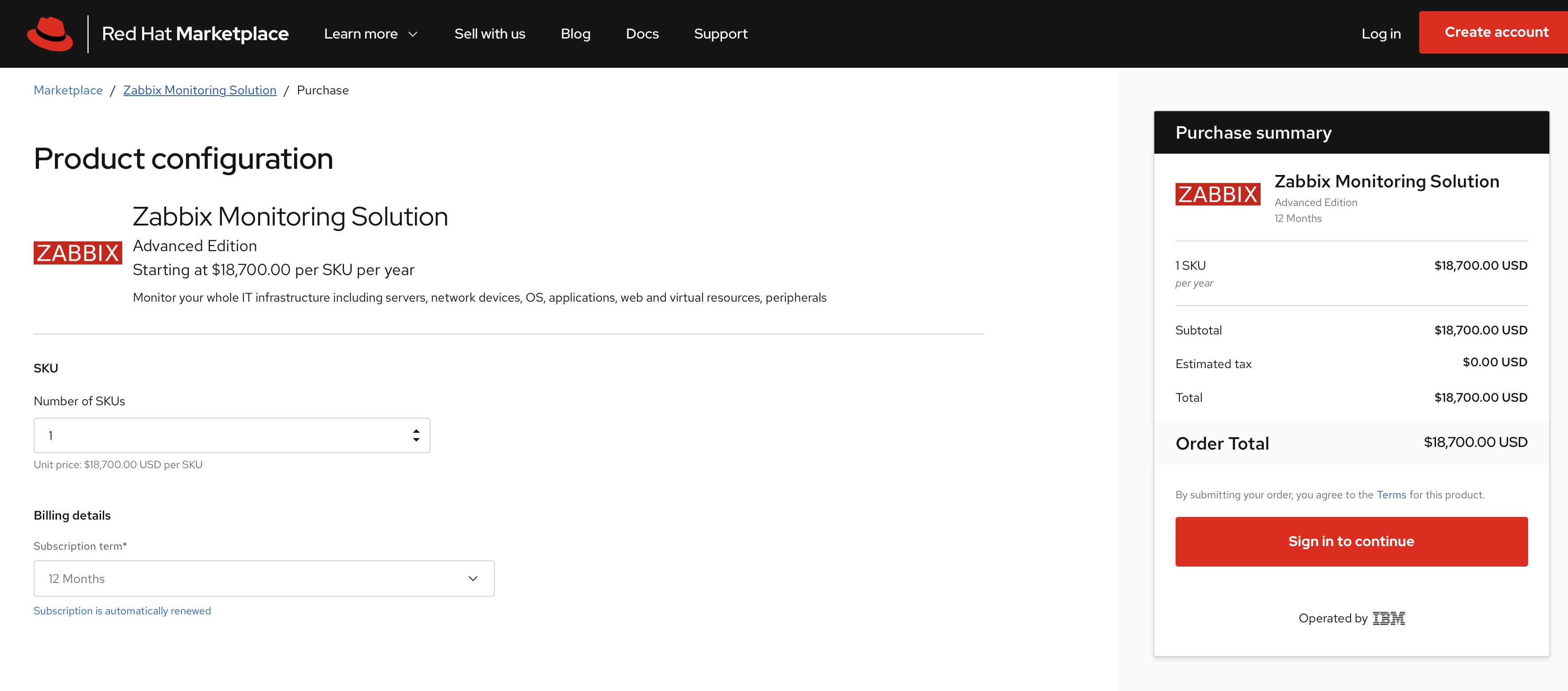
5. Navigate to your software within Red Hat Marketplace and install the Zabbix Operator software as specified in the image.
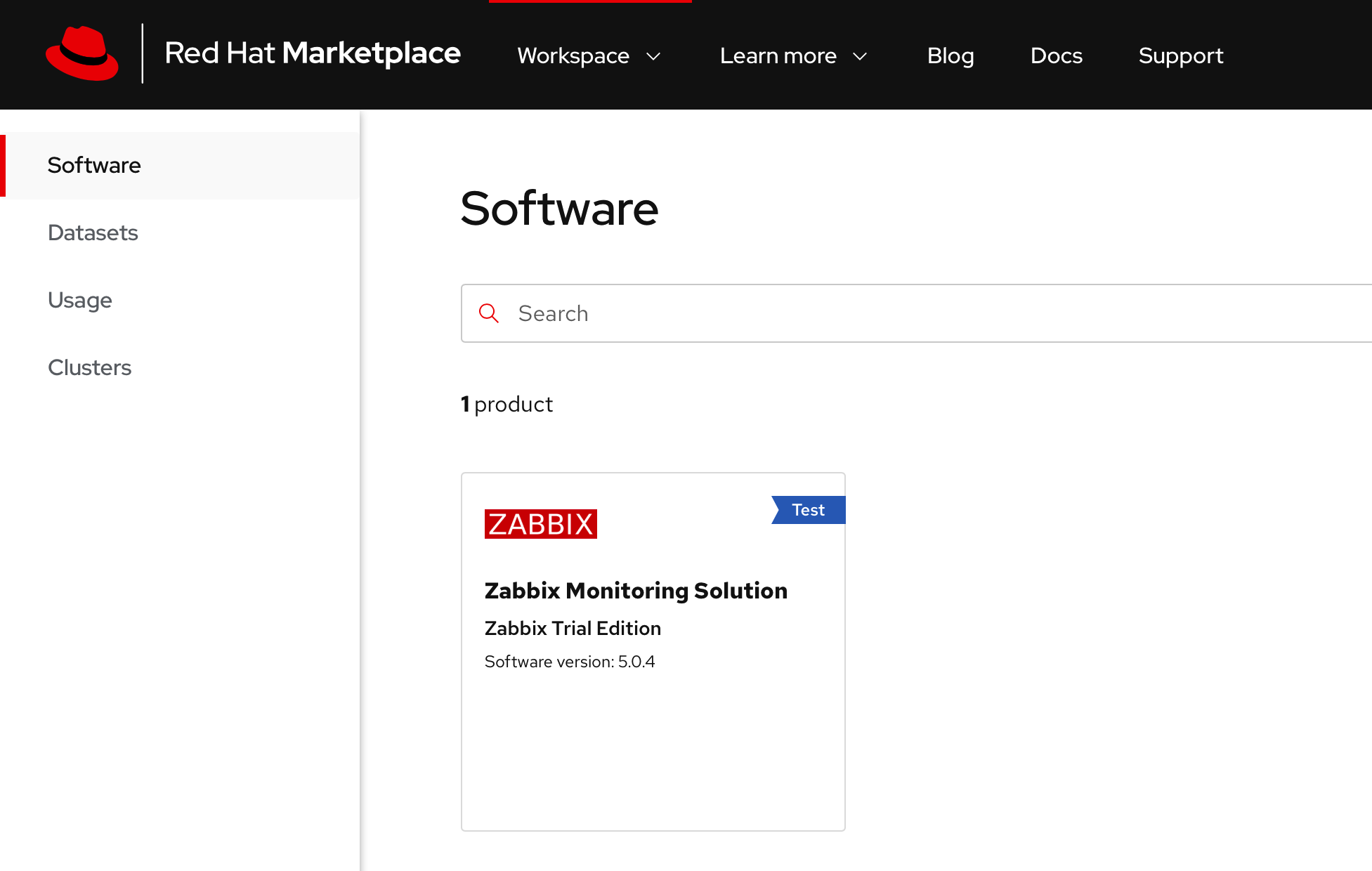
6. Install the Operator. Set the update approval strategy to Automatic to ensure that you always have the latest version of Zabbix components installed.
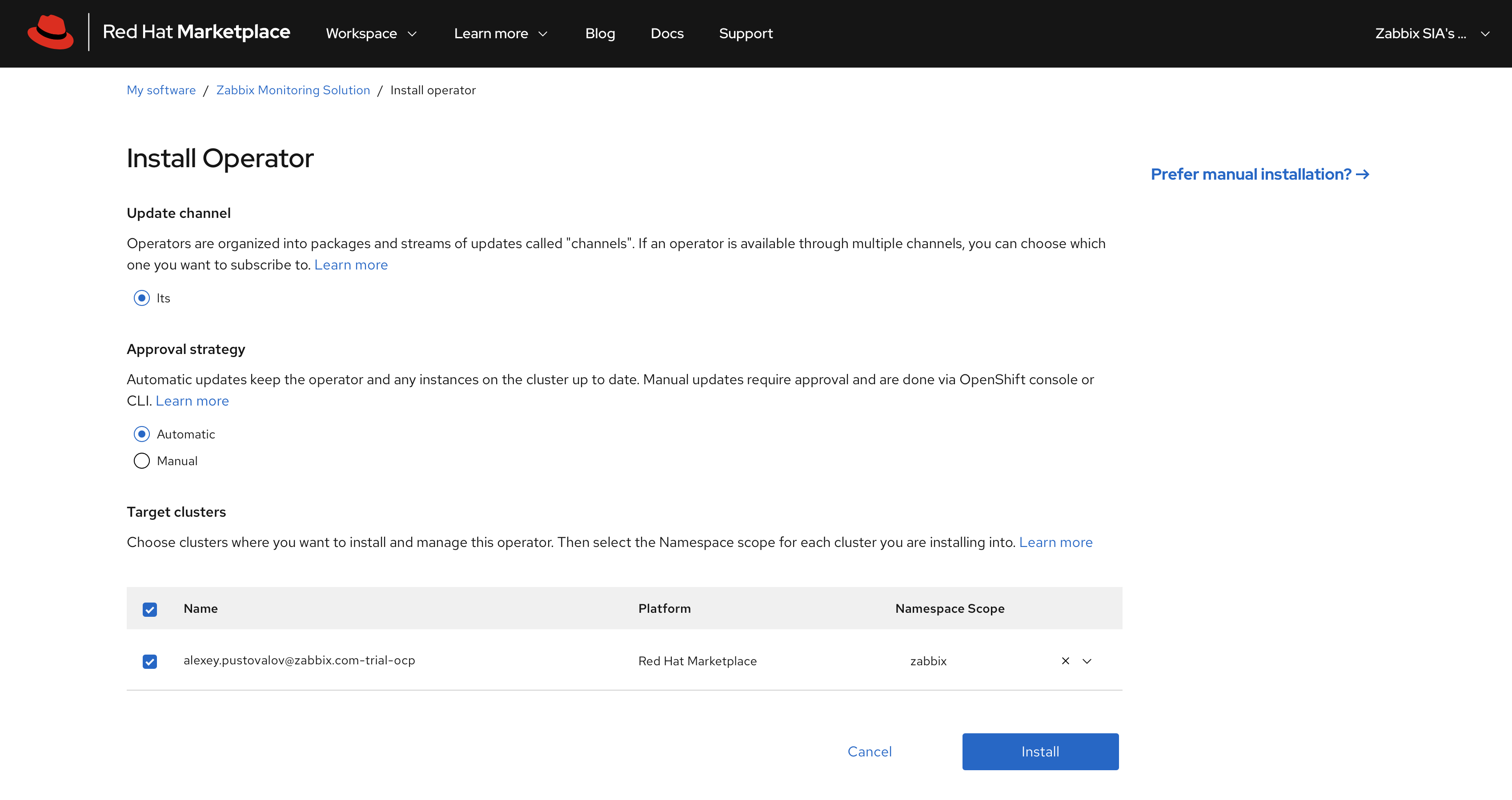
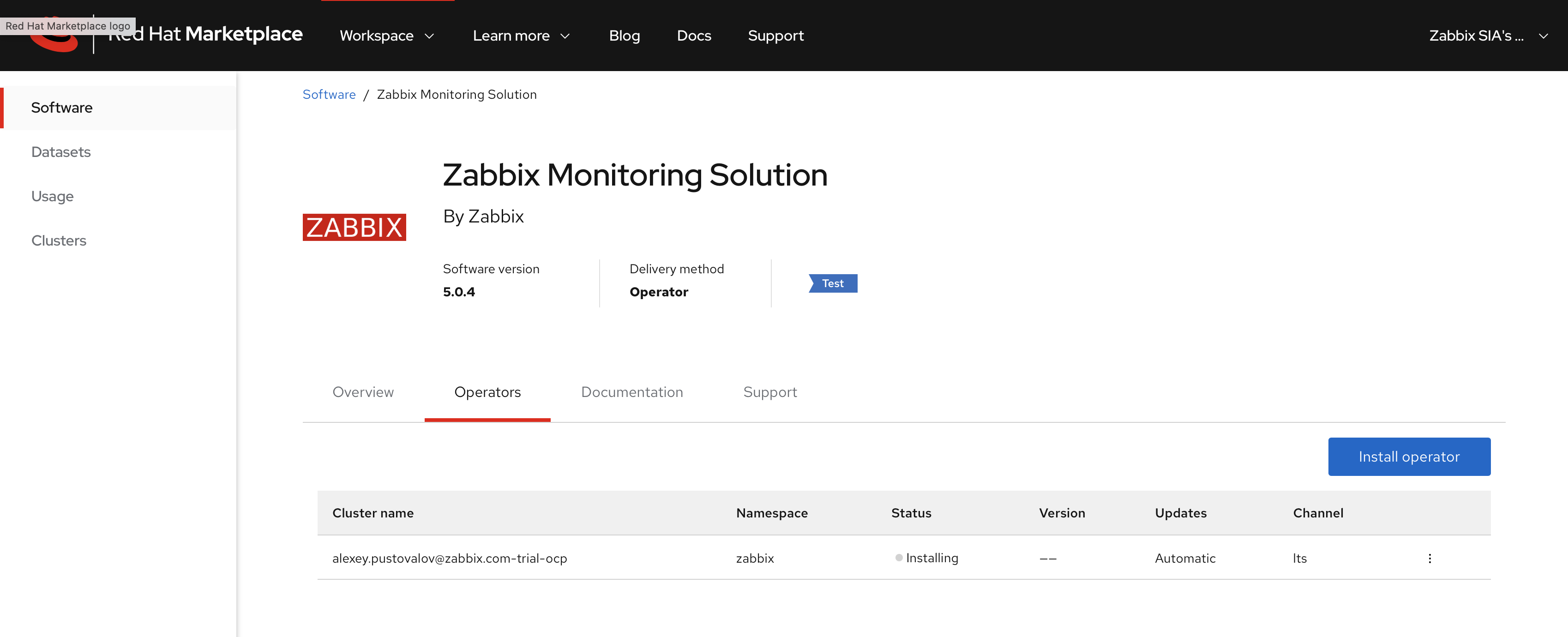
7. The Zabbix Operator is now installed into your specified cluster.
8. Go to Operators → Installed Operators.
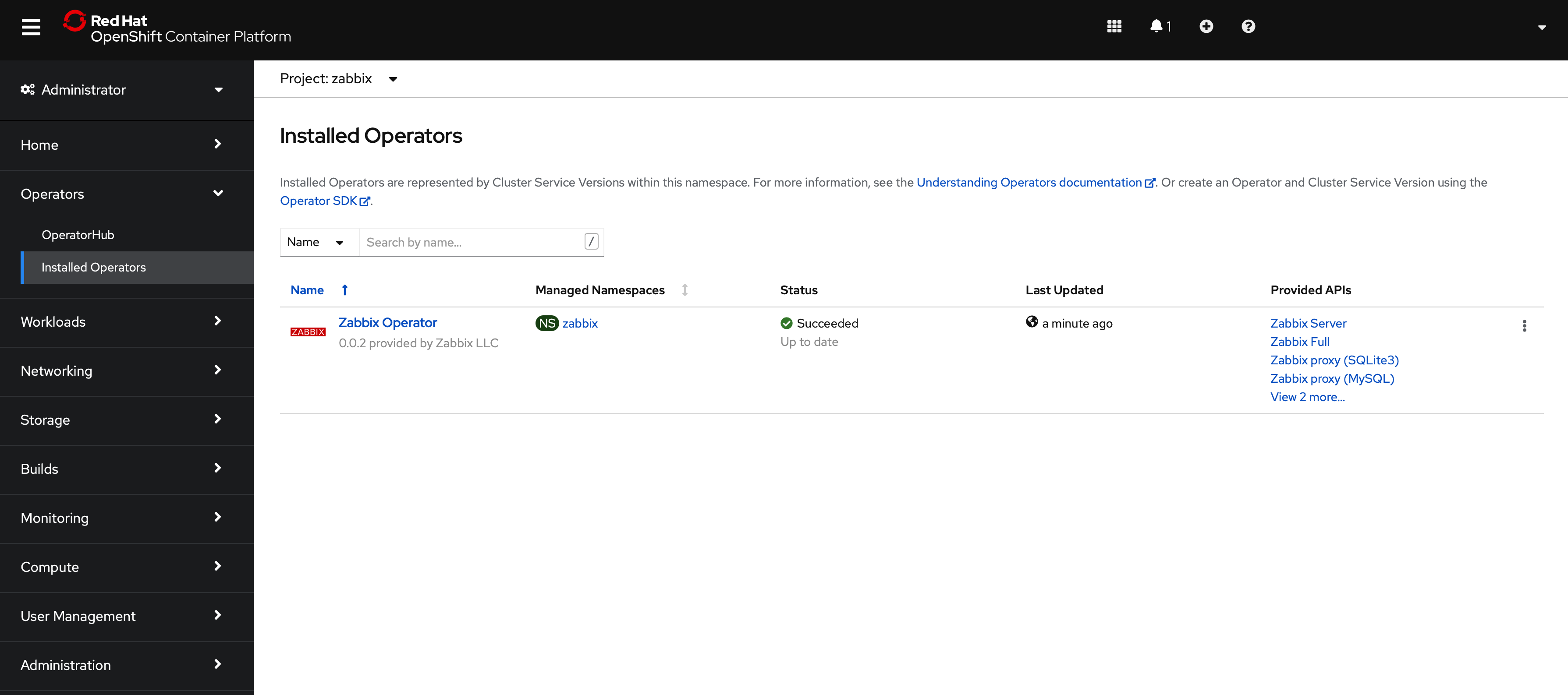
9. Open the "Zabbix Operator" configuration page.
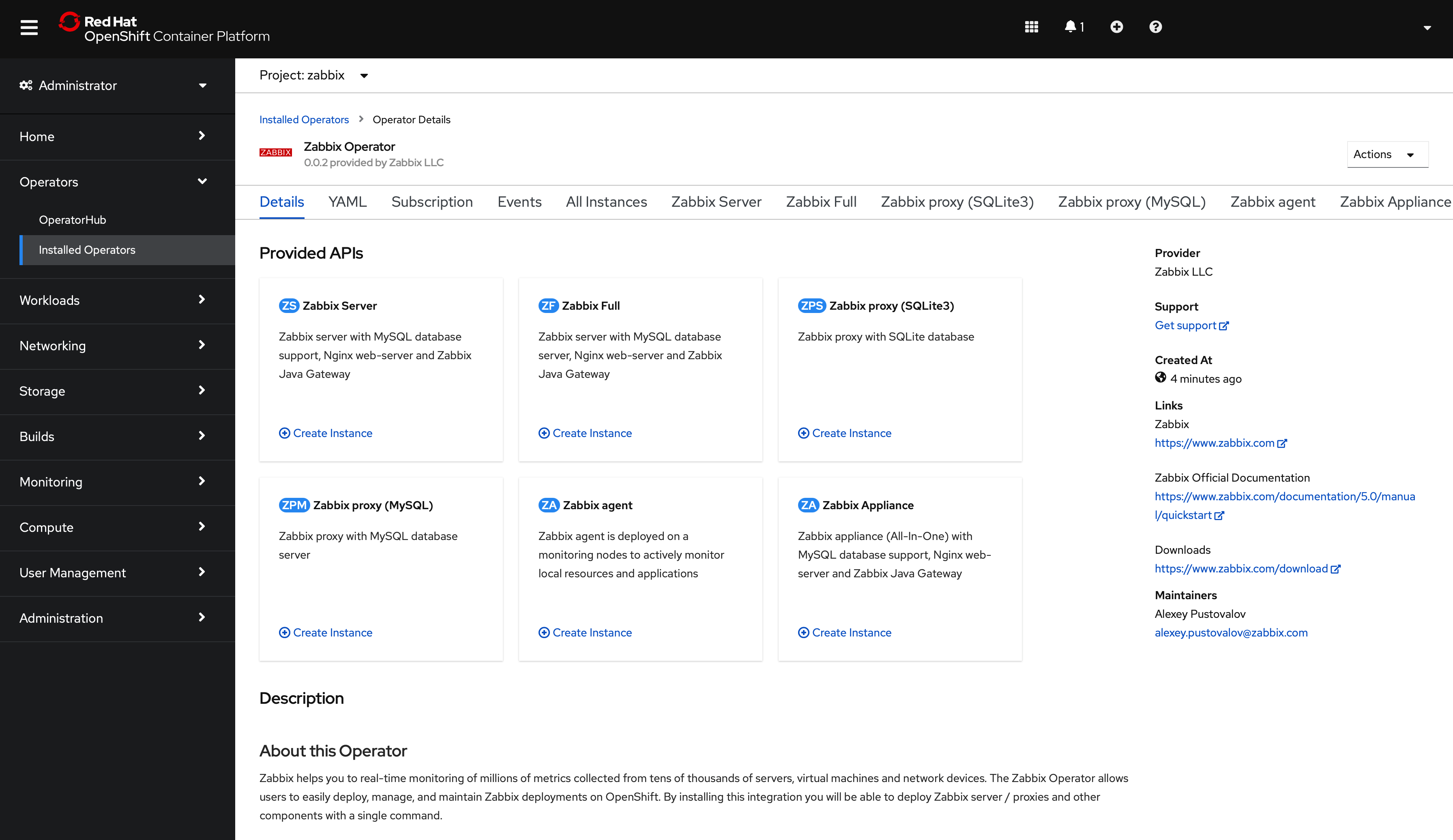
Using OperatorHub
If you have installed OpenShift in AWS ensure that the requisite ports are opened for the worker nodes’ security group.
1. Select OperatorHub from the Operators submenu and search for Zabbix.

2. Select Zabbix Operator and click on Install.
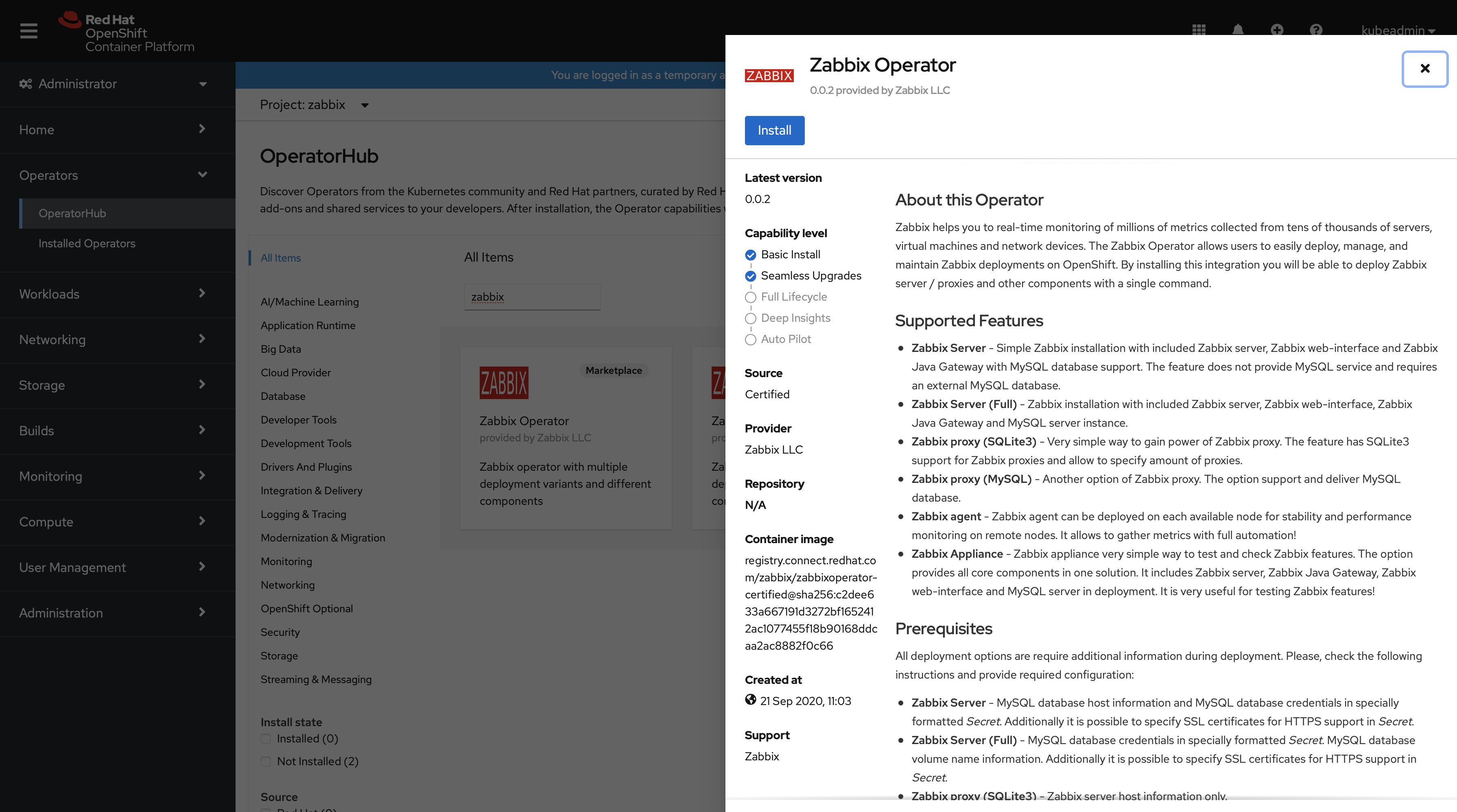
3. Select the installation options.
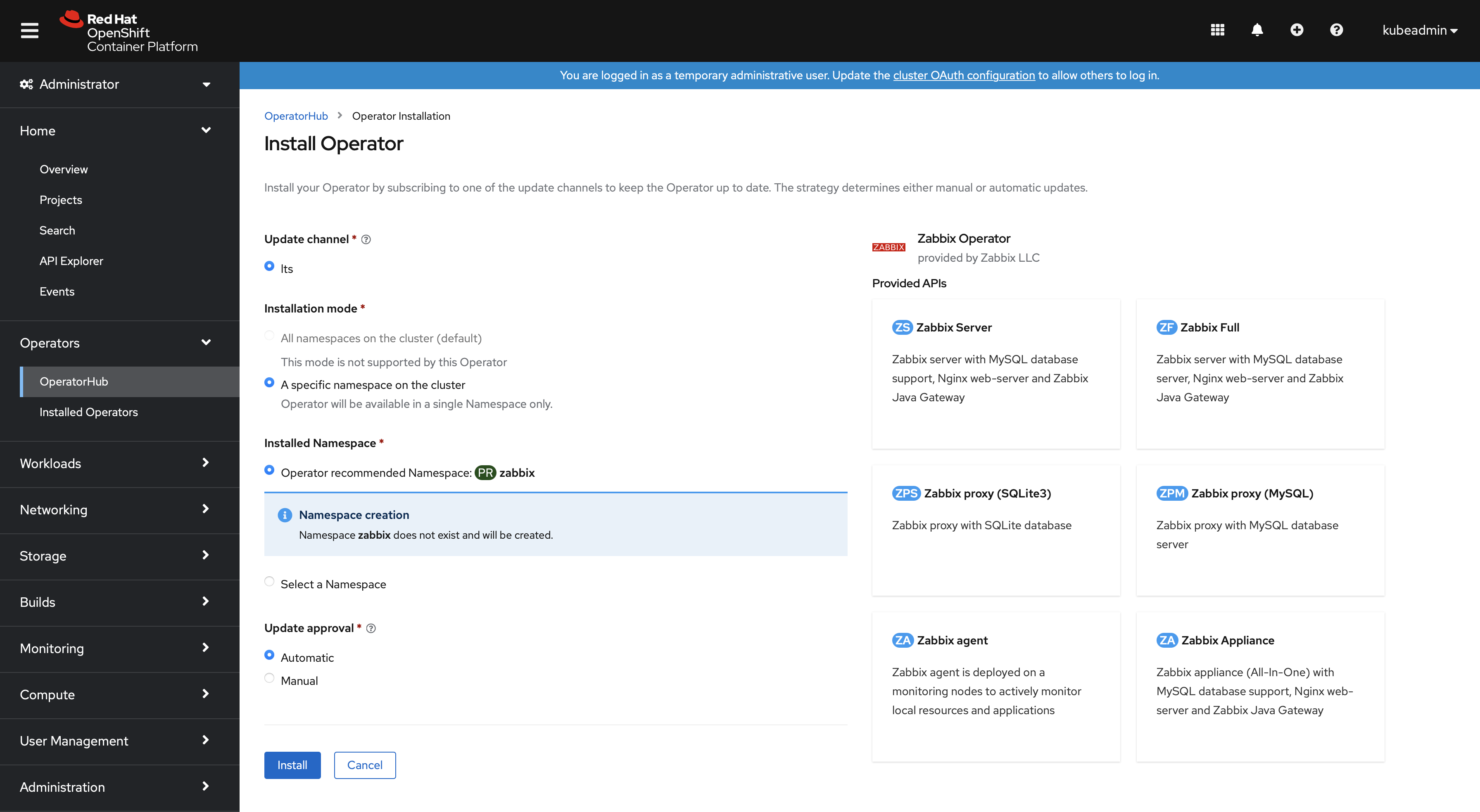
4. Go to Operators → Installed Operators.
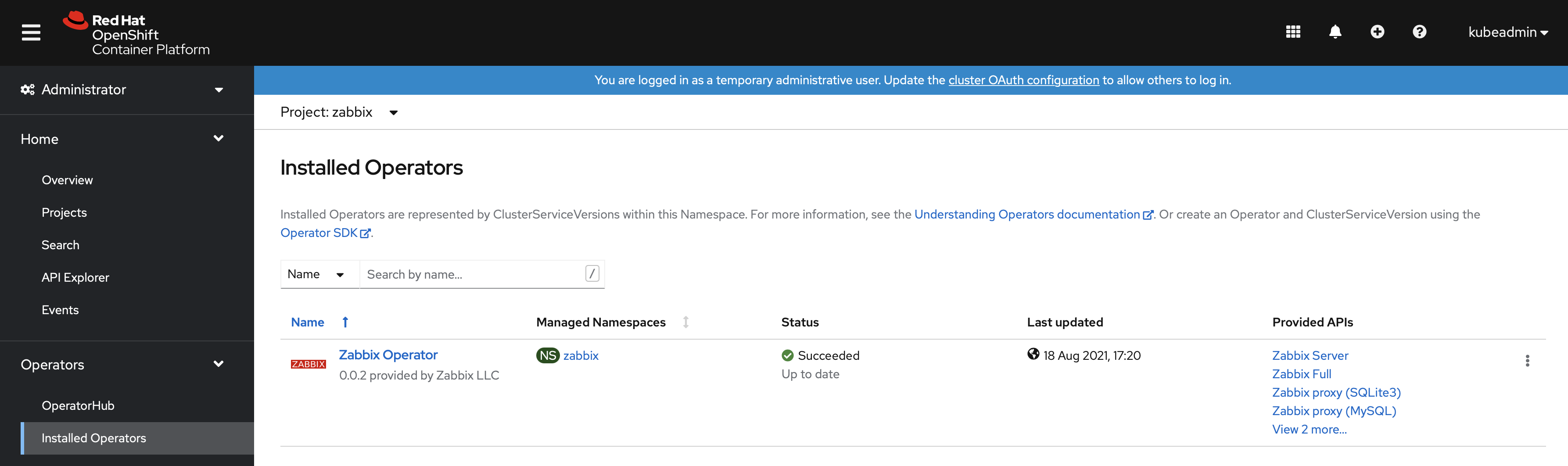
5. Open the "Zabbix Operator" configuration page.
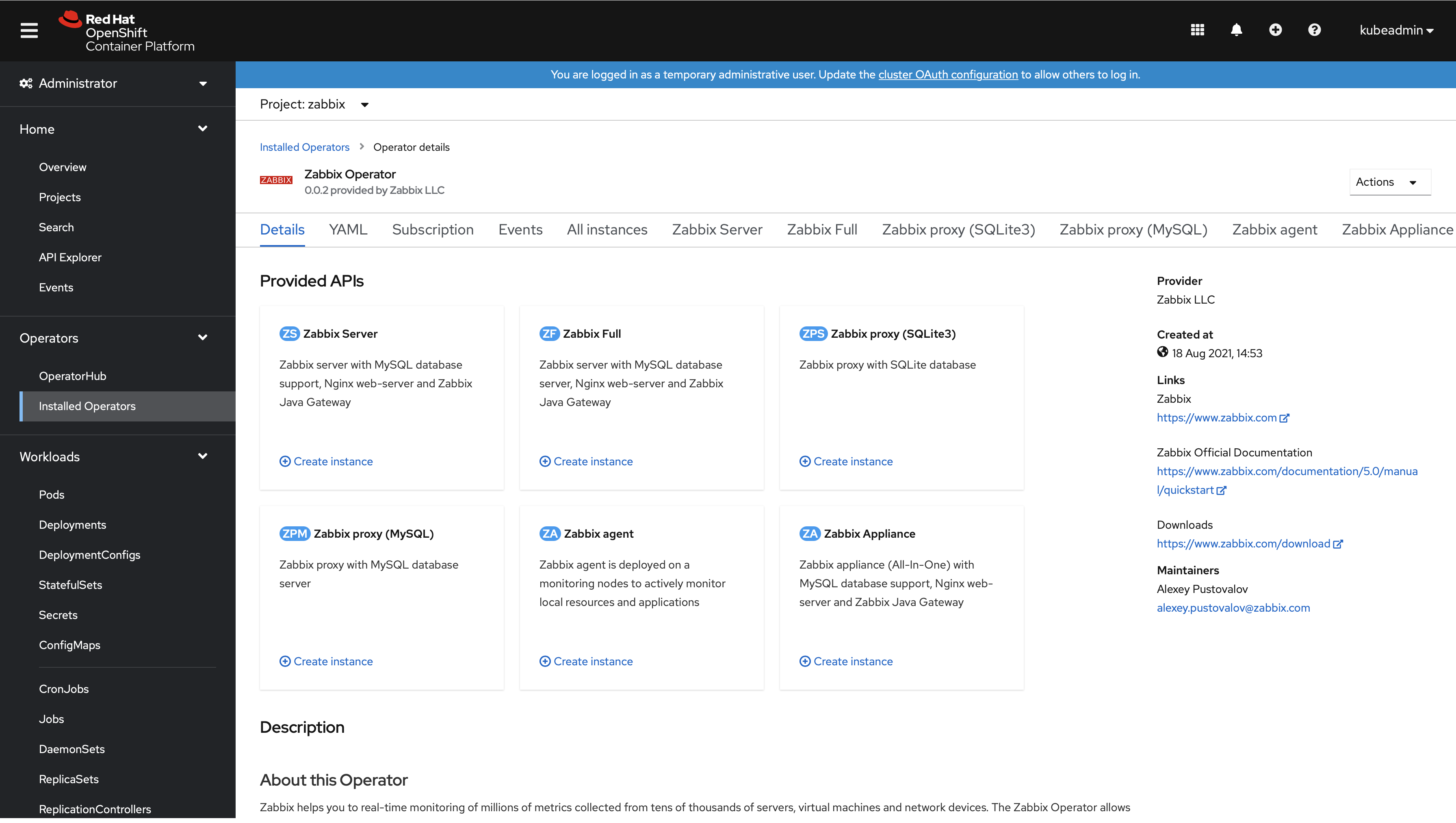
Configuration
Some of the operands (installation options) require additional resources to be created before. The following section describes these prerequisites. All possible configuration options are available during operand deployment. For example, Zabbix proxy (MySQL):
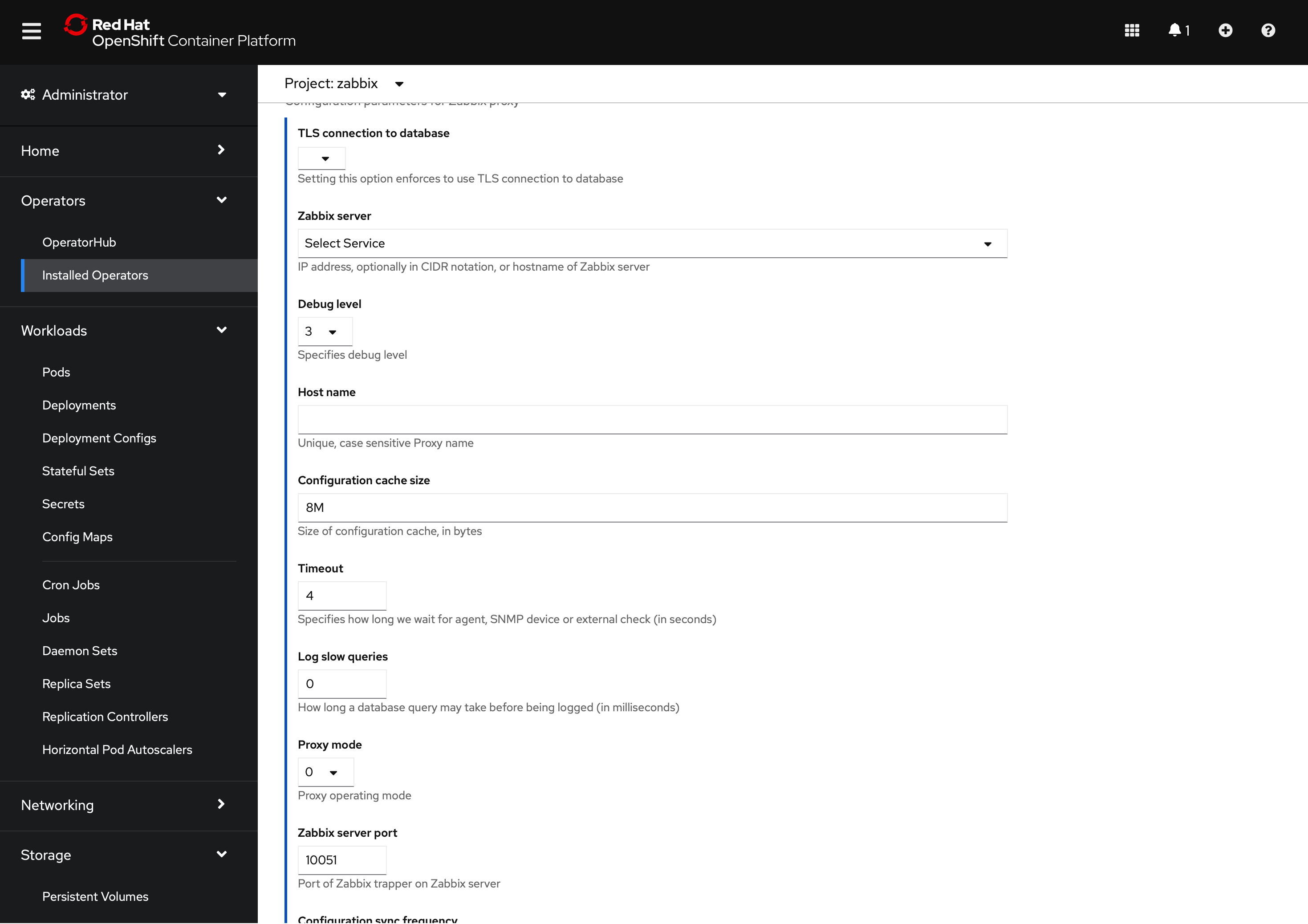
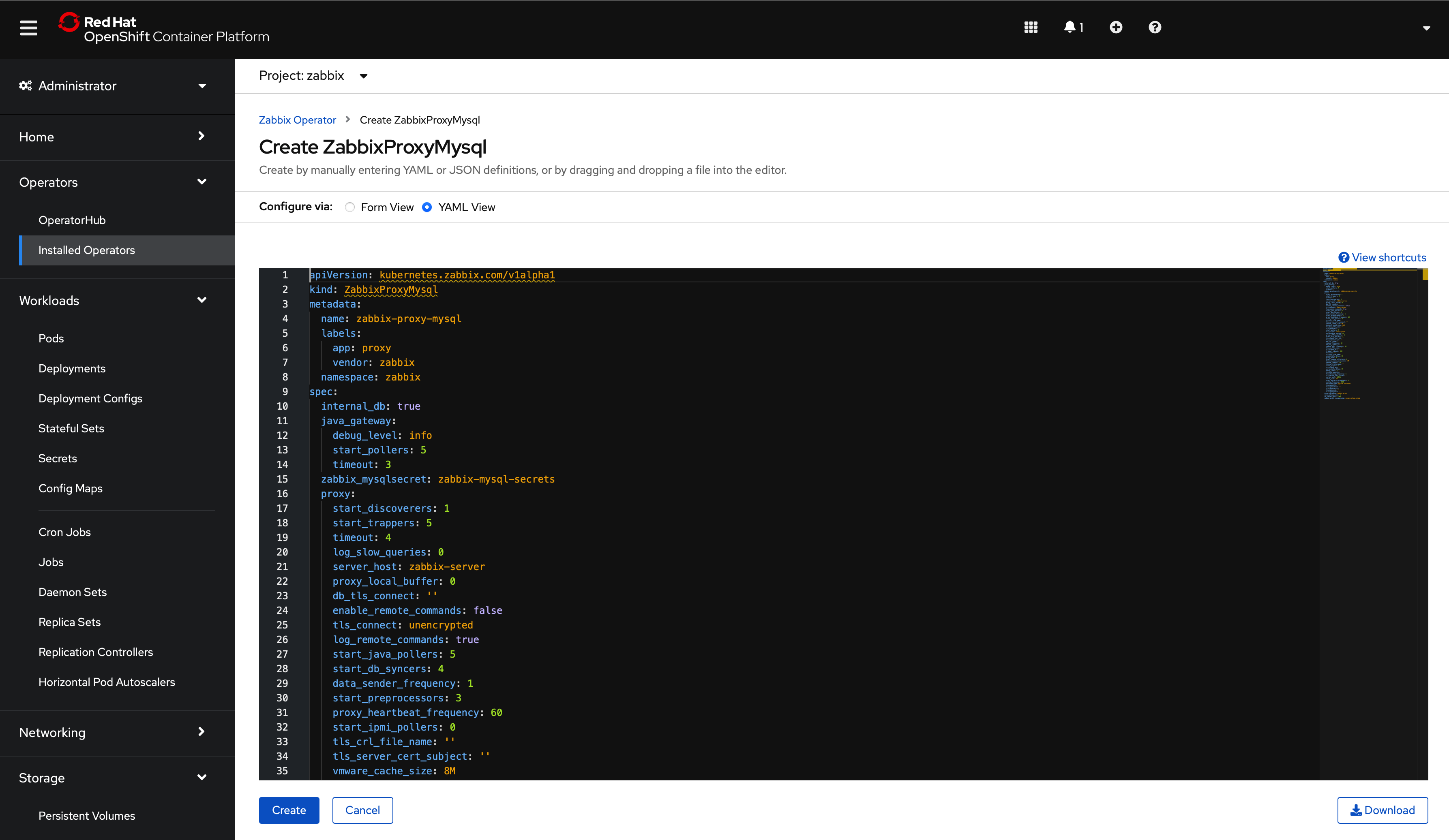
The YAML section provides all available options with default values:
Zabbix server
This operand has a few prerequisites:
1. An existing MySQL database entry point - a MySQL database/cluster must be created before running the "Zabbix Server" operand. For example, a standalone MySQL server with persistent volume:
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: mysql-pv-claim
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 20Gi
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: mysql
spec:
selector:
matchLabels:
app: mysql
strategy:
type: Recreate
template:
metadata:
labels:
app: mysql
spec:
containers:
- image: mysql:8.0
name: mysql
args:
- mysqld
- '--character-set-server=utf8'
- '--collation-server=utf8_bin'
- '--default-authentication-plugin=mysql_native_password'
env:
# Use secret in real usage
- name: MYSQL_ROOT_PASSWORD
value: Welcome1!
ports:
- containerPort: 3306
name: mysql
volumeMounts:
- name: mysql-persistent-storage
mountPath: /var/lib/mysql
volumes:
- name: mysql-persistent-storage
persistentVolumeClaim:
claimName: mysql-pv-claim
---
apiVersion: v1
kind: Service
metadata:
name: mysql
spec:
ports:
- port: 3306
selector:
app: mysql
clusterIP: NonePlease, note that Zabbix does not support a utf8_mb4 charset and default caching_sha2_password authentication plugin.
2. MySQL credentials using secret - must be secret with mysql_root_password, mysql_zabbix_username and mysql_zabbix_password data. For example:
kind: Secret
apiVersion: v1
metadata:
name: zabbix-server-secrets
data:
mysql_root_password: V2VsY29tZTEh
mysql_zabbix_password: emFiYml4X3N1cGVyIQ==
mysql_zabbix_username: emFiYml4
type: Opaquewhere all fields are encoded using base64. For example:
An example of "Zabbix Server" operand configuration:
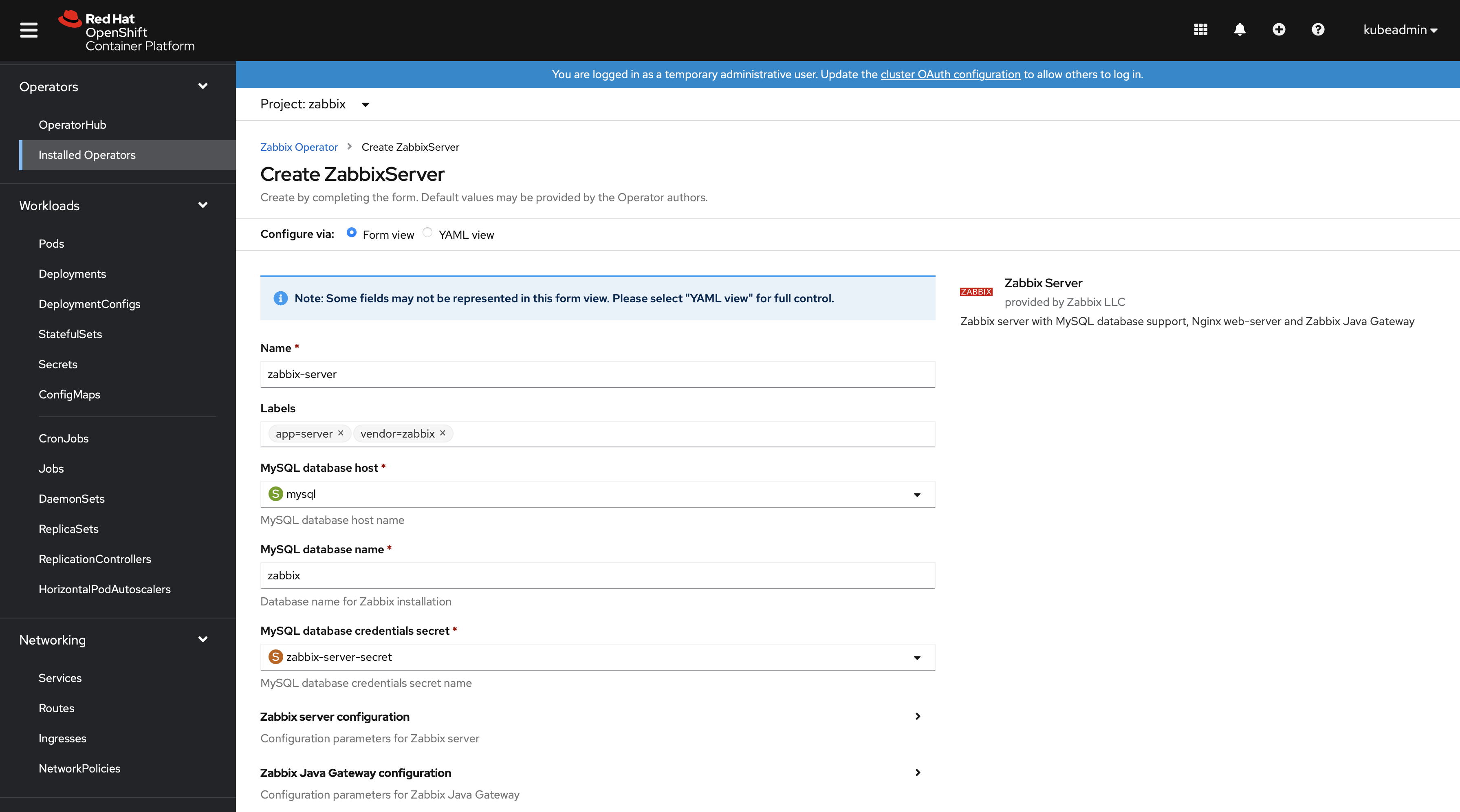
All configuration options are available using the form view, but it is possible to use the YAML view as well. For example:
Finally, the operand will create multiple pods. It is possible to examine them in the Workloads → Pods section:
The route for Zabbix web interface is located under Networking → Routes. The URL provides access to the Zabbix web interface. In the following example it is http://zabbix-server-zabbix.apps-crc.testing/:
Zabbix full
This operand has a few prerequisites:
1. MySQL volume claim - must be persistent volume claim. For example:
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: zabbix-database
namespace: zabbix
spec:
accessModes:
- ReadWriteOnce
volumeMode: Filesystem
resources:
requests:
storage: 50Gi2. MySQL credentials using secret - must be secret with mysql_root_password, mysql_zabbix_username and mysql_zabbix_password data. For example:
kind: Secret
apiVersion: v1
metadata:
name: zabbix-full-secrets
data:
mysql_root_password: V2VsY29tZTEh
mysql_zabbix_password: emFiYml4X3N1cGVyIQ==
mysql_zabbix_username: emFiYml4
type: Opaquewhere all fields are encoded using base64. For example:
An example of "Zabbix Full" operand configuration:
All configuration options are available using the form view, but it is possible to use the YAML view as well. For example:
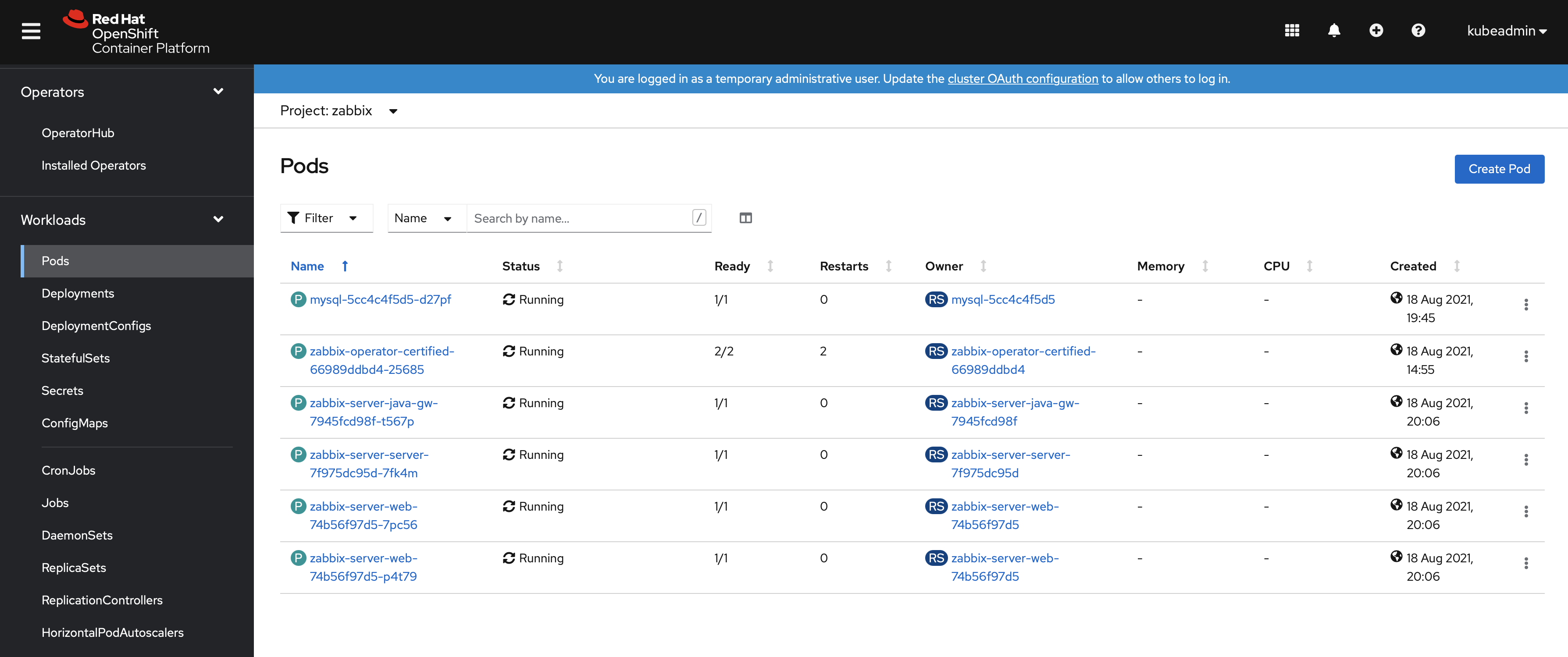
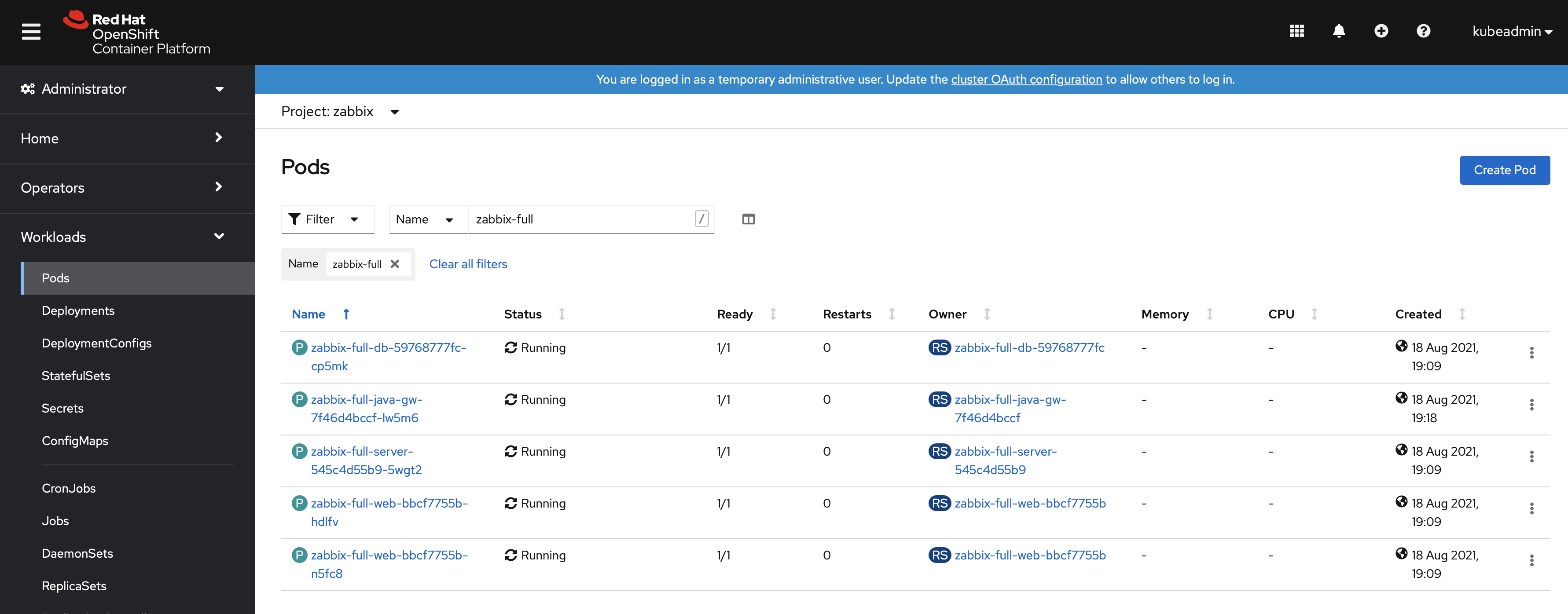
Finally, the operand will create multiple pods. It is possible to examine them in the Workloads → Pods section:
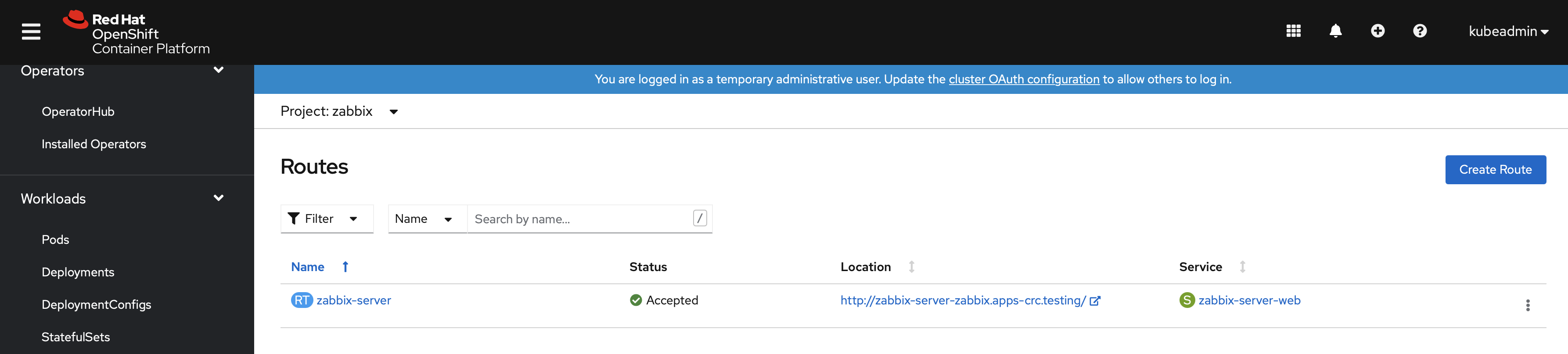
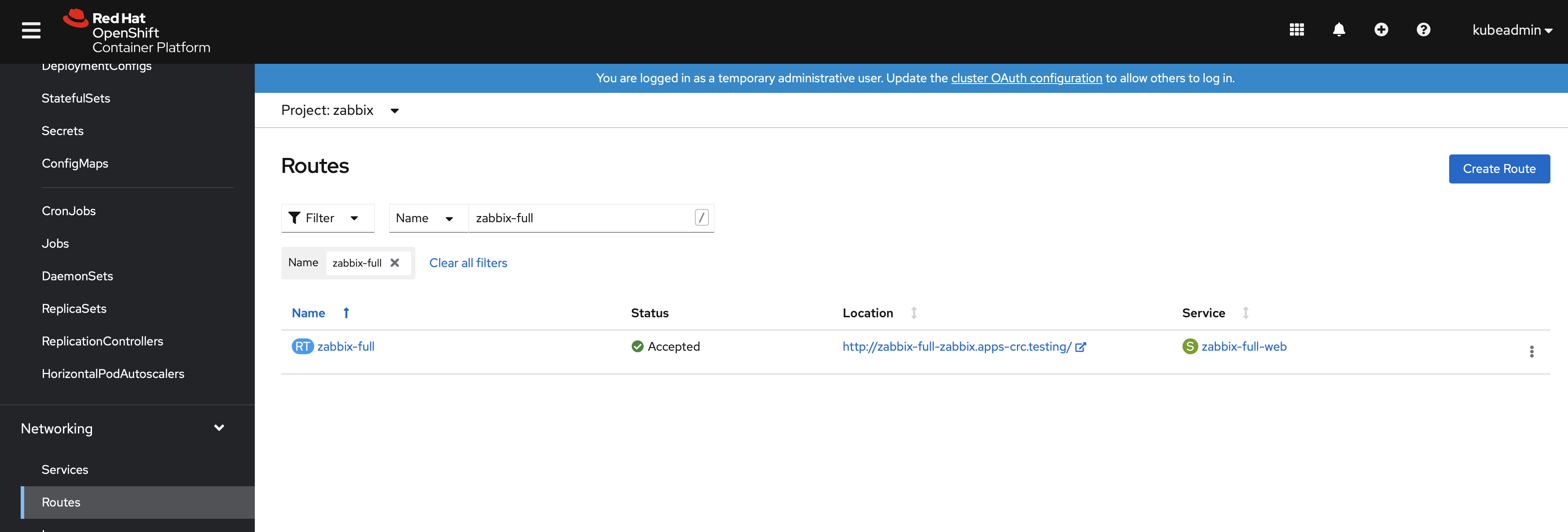
The route for Zabbix web interface is located under Networking → Routes. The URL provides access to the Zabbix web interface. In the following example it is http://zabbix-full-zabbix.apps-crc.testing/:
Zabbix proxy (SQLite3)
An example of "Zabbix proxy (SQLite3)" operand configuration:
Finally, the operand will create multiple pods. It is possible to examine them in the Workloads → Pods section:
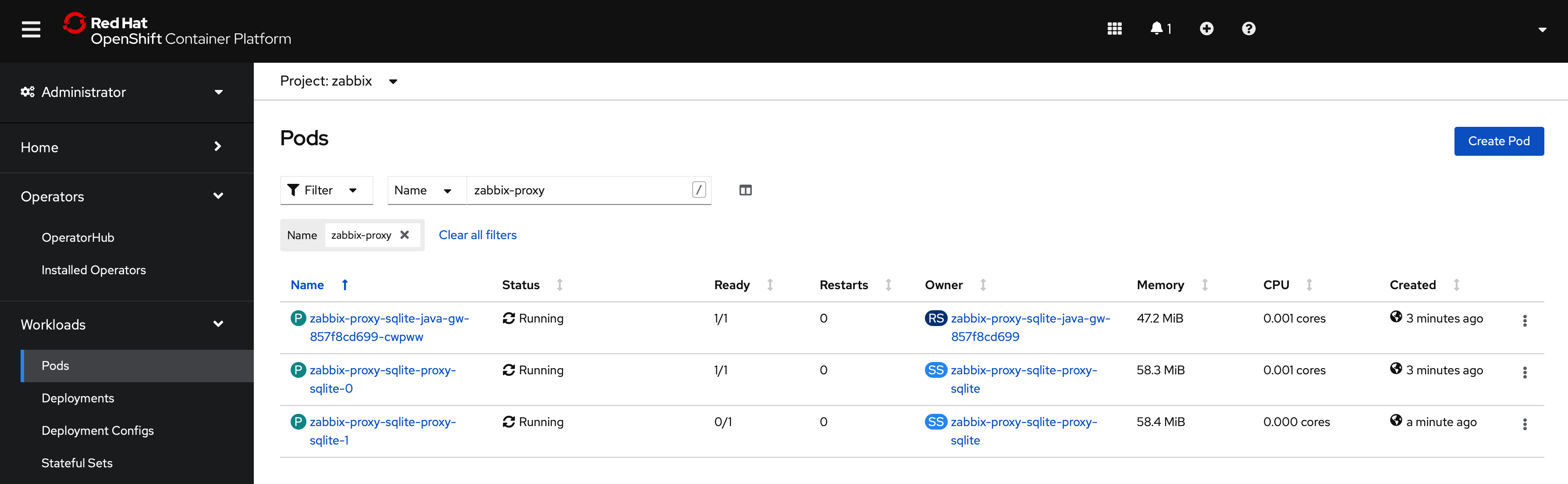
Additional information
Creating new secret
The following procedure describes how to create a new secret using Openshift Console.
1. Open the Workloads → Secrets section and switch project to the Zabbix Operator project (by default, "zabbix").
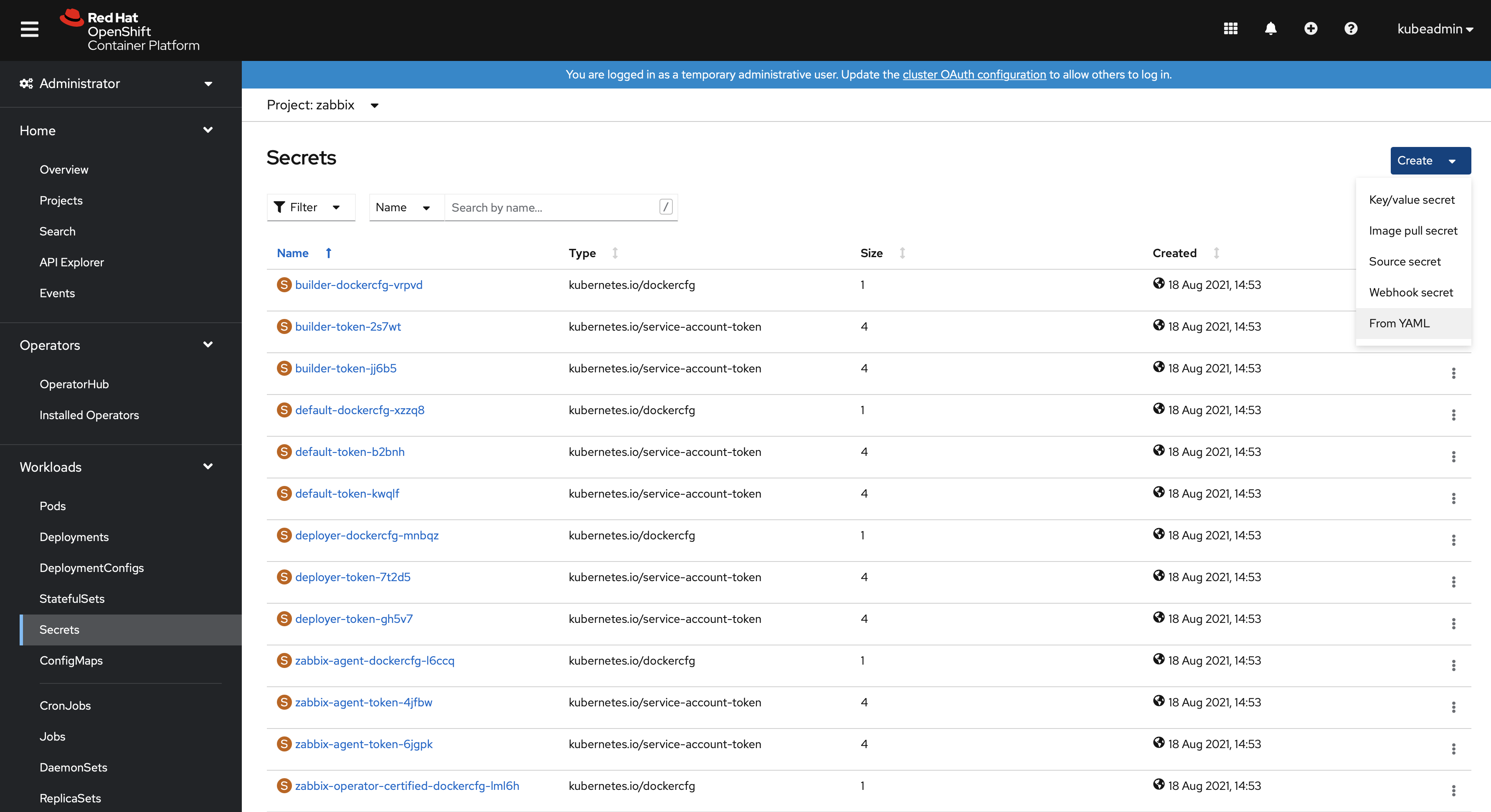
2. Create a new secret using the From YAML option.
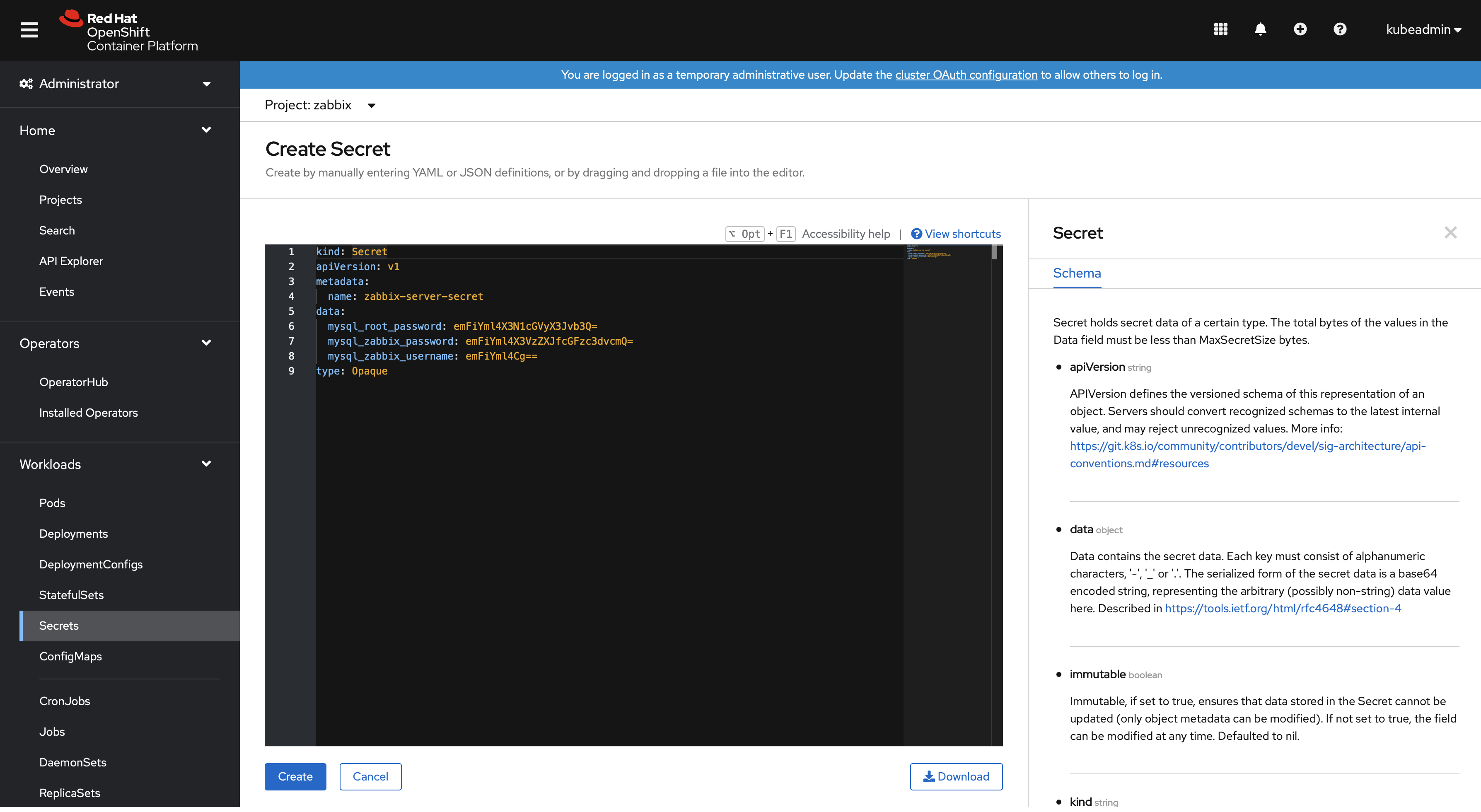
SSL certificates for HTTPS
It is possible to enable HTTPS directly in the Zabbix web interface pods. In this case create the following secret using the YAML option:
kind: Secret
apiVersion: v1
metadata:
name: zabbix-web-sslsecret
data:
ssl.crt: >-
< ssl.crt data>
ssl.key: >-
< ssl.key data >
dhparam.pem: >-
< dhparam.pem data >The names of certificates and DH Parameters file are statics. Please use the listed in the above example only!
MySQL database certificate base encryption
MySQL database side:
apiVersion: v1
data:
root-ca.pem: >-
< root-ca.pem data>
server-cert.pem: >-
< server-cert.pem data>
server-key.pem: >-
< server-key.pem data>
kind: Secret
metadata:
name: zabbix-db-server-tls-secret
type: OpaqueZabbix components side:
apiVersion: v1
data:
client-cert.pem: >-
< client-cert.pem data>
client-key.pem: >-
< client-key.pem data>
root-ca.pem: >-
< root-ca.pem data>
kind: Secret
metadata:
name: zabbix-db-client-tls-secret
type: OpaqueCertificates must include "-----BEGIN RSA PRIVATE KEY-----" and "-----END RSA PRIVATE KEY-----". For example:
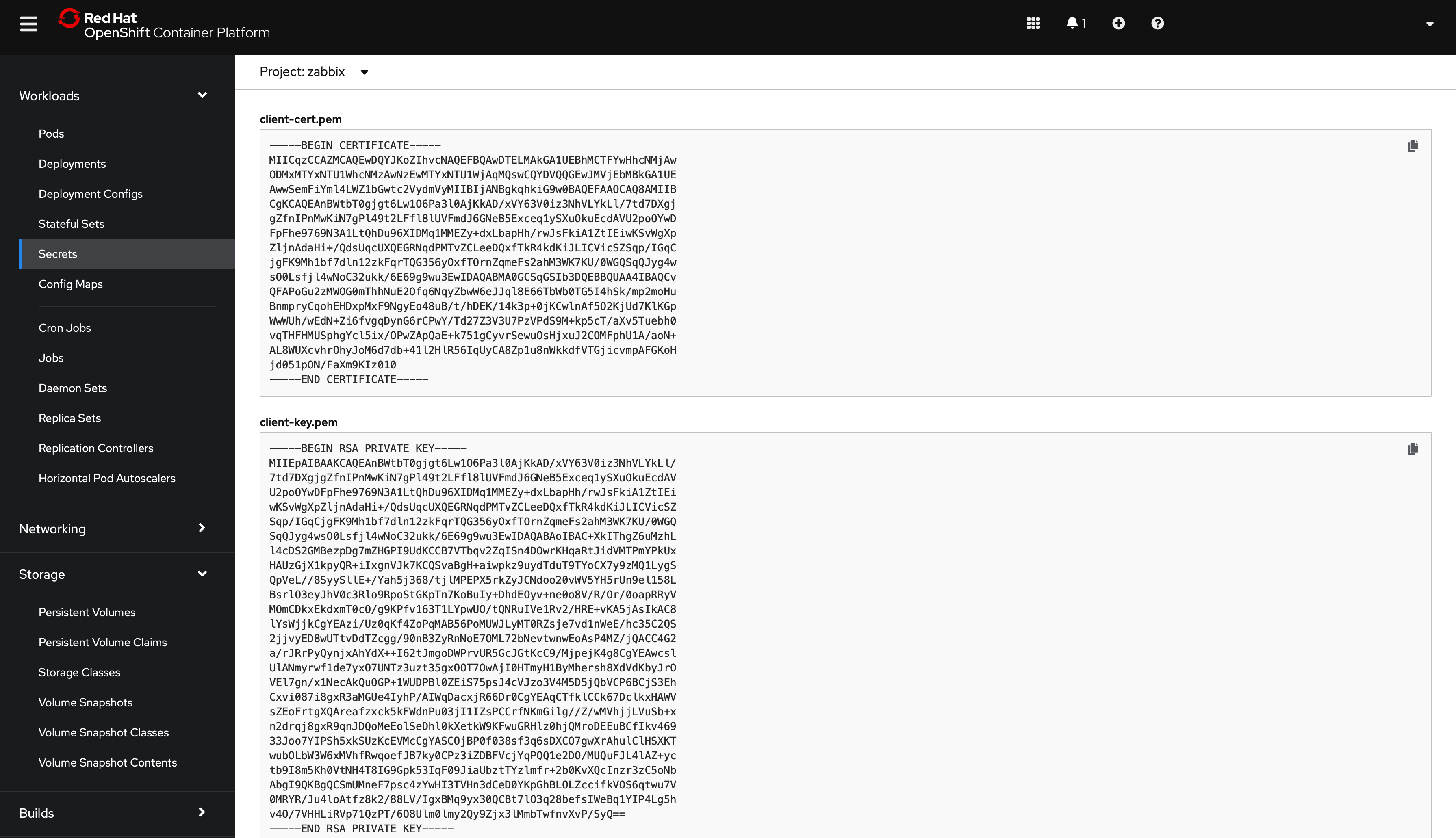
Then, during deployment, in the Zabbix component section and MySQL server (if using built-in server) choose the proper "TLS connection to database" option value and the "MySQL database certificates (client)" secret value.
Known issues
- Zabbix agent does not have the possibility to determine proper node name. It always has dynamic hostname.

