Is this not what you were looking for? Switch to the current version or choose one from the drop-down menu.
1 Proxies
Overview
A Zabbix proxy can collect performance and availability data on behalf of the Zabbix server. This way, a proxy can take on itself some of the load of collecting data and offload the Zabbix server.
Also, using a proxy is the easiest way of implementing centralized and distributed monitoring, when all agents and proxies report to one Zabbix server and all data is collected centrally.
A Zabbix proxy can be used to:
- Monitor remote locations
- Monitor locations having unreliable communications
- Offload the Zabbix server when monitoring thousands of devices
- Simplify the maintenance of distributed monitoring
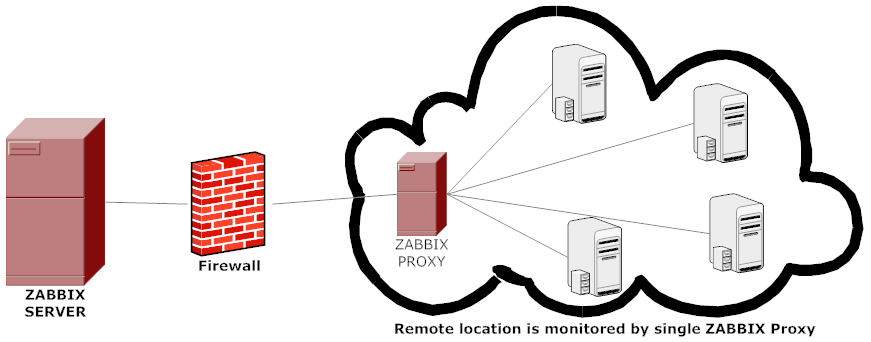
The proxy requires only one TCP connection to the Zabbix server. This way it is easier to get around a firewall as you only need to configure one firewall rule.
Zabbix proxy must use a separate database. Pointing it to the Zabbix server database will break the configuration.
All data collected by the proxy is stored locally before transmitting it over to the server. This way no data is lost due to any temporary communication problems with the server. The ProxyLocalBuffer and ProxyOfflineBuffer parameters in the proxy configuration file control for how long the data are kept locally.
It may happen that a proxy, which receives the latest configuration changes directly from Zabbix server database, has a more up-to-date configuration than Zabbix server whose configuration may not be updated as fast due to the value of CacheUpdateFrequency. As a result, proxy may start gathering data and send them to Zabbix server that ignores these data.
Zabbix proxy is a data collector. It does not calculate triggers, process events or send alerts. For an overview of what proxy functionality is, review the following table:
| Function | Supported by proxy | |
|---|---|---|
| Items | ||
| Zabbix agent checks | Yes | |
| Zabbix agent checks (active) | Yes 1 | |
| Simple checks | Yes | |
| Trapper items | Yes | |
| SNMP checks | Yes | |
| SNMP traps | Yes | |
| IPMI checks | Yes | |
| JMX checks | Yes | |
| Log file monitoring | Yes | |
| Internal checks | Yes | |
| SSH checks | Yes | |
| Telnet checks | Yes | |
| External checks | Yes | |
| Built-in web monitoring | Yes | |
| Network discovery | Yes | |
| Low-level discovery | Yes | |
| Calculating triggers | No | |
| Processing events | No | |
| Sending alerts | No | |
| Remote commands | No | |
[1] To make sure that an agent asks the proxy (and not the server) for active checks, the proxy must be listed in the ServerActive parameter in the agent configuration file.
Configuration
Once you have installed and configured a proxy, it is time to configure it in the Zabbix frontend.
Adding proxies
To configure a proxy in Zabbix frontend:
- Go to: Administration → Proxies
- Click on Create proxy
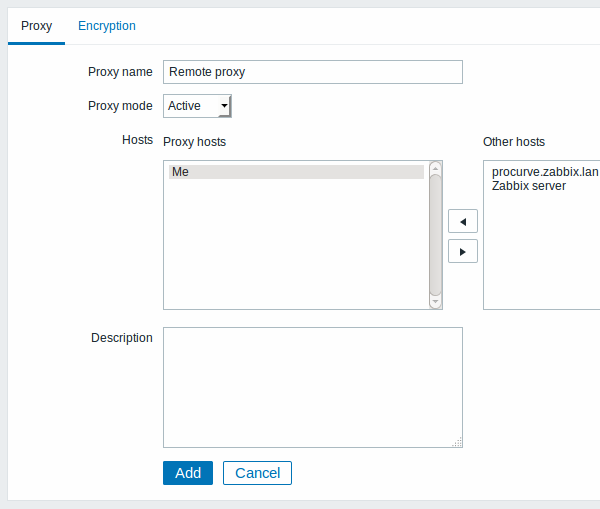
| Parameter | Description |
|---|---|
| Proxy name | Enter the proxy name. It must be the same name as in the Hostname parameter in the proxy configuration file. |
| Proxy mode | Select the proxy mode. Active - the proxy will connect to the Zabbix server and request configuration data Passive - Zabbix server connects to the proxy Note that without encrypted communications (sensitive) proxy configuration data may become available to parties having access to the Zabbix server trapper port when using an active proxy. This is possible because anyone may pretend to be an active proxy and request configuration data if authentication does not take place. |
| Hosts | Add hosts to be monitored by the proxy. |
| Description | Enter the proxy description. |
The Encryption tab allows you to require encrypted connections with the proxy.
| Parameter | Description |
|---|---|
| Connections to proxy | How the server connects to the passive proxy: no encryption (default), using PSK (pre-shared key) or certificate. |
| Connections from proxy | Select what type of connections are allowed from the active proxy. Several connection types can be selected at the same time (useful for testing and switching to other connection type). Default is "No encryption". |
| Issuer | Allowed issuer of certificate. Certificate is first validated with CA (certificate authority). If it is valid, signed by the CA, then the Issuer field can be used to further restrict allowed CA. This field is optional, intended to use if your Zabbix installation uses certificates from multiple CAs. |
| Subject | Allowed subject of certificate. Certificate is first validated with CA. If it is valid, signed by the CA, then the Subject field can be used to allow only one value of Subject string. If this field is empty then any valid certificate signed by the configured CA is accepted. |
| PSK identity | Pre-shared key identity string. Do not put sensitive information in the PSK identity, it is transmitted unencrypted over the network to inform a receiver which PSK to use. |
| PSK | Pre-shared key (hex-string). Maximum length: 512 hex-digits (256-byte PSK) if Zabbix uses GnuTLS or OpenSSL library, 64 hex-digits (32-byte PSK) if Zabbix uses mbed TLS (PolarSSL) library. Example: 1f87b595725ac58dd977beef14b97461a7c1045b9a1c963065002c5473194952 |
Host configuration
You can specify that an individual host should be monitored by a proxy in the host configuration form, using the Monitored by proxy field.
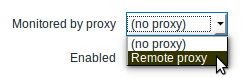
Host mass update is another way of specifying that hosts should be monitored by a proxy.

